The MEV Edition (part I) | DeFi Download
Learning about MEV from TradFi; The "MEV Supply Chain"; MEV attacks; The Future of MEV
Dear Bankless Nation 🏴,
Looking back at what web3 has accomplished since 2018, we have a lot to be proud of. DeFi took off like a rocket bringing new entrants, DAOs got their legs, and NFTs have become a household term. But looking into the future of blockchains and web3, there are some clouds. Maximum Extractable Value (MEV) is quickly becoming a problem, and an existential one at that.
Information about prices and markets allows markets to stay liquid, but there is a centralizing effect when the entities that find MEV also finalize transactions. MEV threatens the decentralization of crypto-economic protocols, but these are not unsolvable problems.
In this edition of the DeFi Download, we give you the run-down on what MEV looks like in TradFi, the different players of the MEV supply chain, and what the future may hold for MEV. We also give you a fun example of an MEV attack and a bit of karma for the harvester. Afterwards, we discuss the burning of tokens and how that burn affects token supply before diving into the economic attack on the Mango protocol.
And as always, we keep you up to date on the latest project releases and opinions on DeFi. Make space in your brain’s hard drive, because this DeFi Download is a fun one!
Contributors: BanklessDAO Writers Guild (Austin Foss, Chameleon, Elemental, Kornekt, oxdog.eth, Teeleroo, Jake and Stake)
This is the official newsletter of BanklessDAO. To unsubscribe, edit your settings.
The MEV Edition (Part I)

MEV in Traditional Finance
Author: Jake and Stake
While MEV is a new concept to most investors, the principles of MEV are not. In fact, they’ve existed in traditional finance for decades.
High Frequency Trading
Flash Boys, a book by Michael Lewis about high frequency trading (HFT), documents trading firms that created a method to front-run orders placed by investors. But in truth, HFT has existed since the 1930’s when the telegraph was used to communicate financial positions across exchanges. It just wasn’t common until 1983 when the NASDAQ introduced purely electronic trading. Soon after, HFT as we know it today was developed and popularized in the mid 2000’s as the markets began to modernize. As a result, cross market trading began to take off.
Today, small arbitrage opportunities occur all the time in traditional finance. These opportunities arise in milliseconds and are imperceptible to humans, but are perceptible to computers. The profit opportunity for these direction-neutral trades was extremely profitable, and companies would spend exorbitant amounts of money to get an advantage. One company, Spread Networks, spent $300 million constructing a fiber optic cable 827 miles long from Chicago to the Nasdaq data center in New Jersey.
Before the project, trades on the Chicago Mercantile Exchange were transmitted in just 17 milliseconds. After the project, transmission time was 13 milliseconds—4 milliseconds of improvement. Contrast that to the average human blink, which lasts 100 milliseconds.
This 4 millisecond difference—priced at $300 million—improves HFT firms’ ability to see orders to buy a stock, buy the stock before the orders can be executed, and sell the stock to the original purchaser for a slightly higher price.
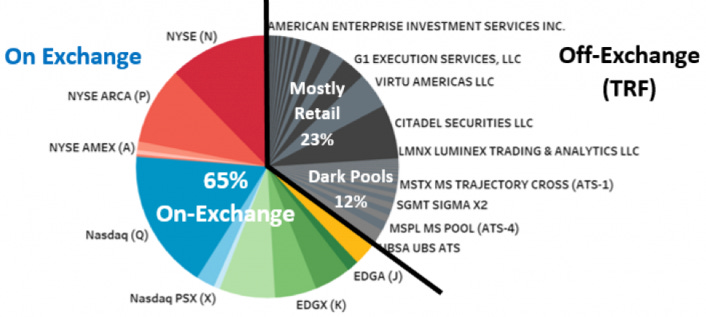
But everyday retail investors purchasing stocks don’t have access to these systems, and are constantly getting front-run by such HFT firms profiting off of retail investors and earning billions of dollars a year. According to the Financial Times, HFT accounted for 65% of US stock market volume in 2008. Some estimate HFT accounted for as much as 78% of total trading volume in 2009.
It’s not all negative externalities though. Arbitrage increases liquidity across markets and closes the difference between bid and ask spreads—leading to better prices. HFT firms skim the difference.
Colocation
In an effort to make their systems as fast as possible, firms went as far as putting their servers inside stock exchange buildings in a strategy called colocation. If they could, they’d do it secretly.
One HFT firm was able to secure a spot “[...] a few feet nearer to an exchange computer[, a spot] that had previously been occupied by machines owned by Toys ‘R’ Us.” As a result, the firm got a slight advantage of just inches, but high frequency trading is a competition measured in microseconds and nanoseconds.
But they knew that if any of their competitors knew about this advantage, they would respond in kind. In fact, the firm with the Toys ‘R’ Us computers was so paranoid about hiding this slight advantage, the HFT firm insisted the Toys ‘R Us logo was not changed after they had moved in.
Efforts to curb the cutthroat HFT dynamic began to arise. Brad Katsuyama was the global head of electronic sales and trading at the Royal Bank of Canada when he noticed that large trades were being taken advantage of by scalpers and resulted in worse prices. After digging deeper, he discovered these fiber optic cables and colocation agreements allowed HFT firms to take advantage of retail traders.
He would then found IEX which is an exchange designed to be a fairer stock trading venue by creating an alternative system. Exchanges like IEX are trying to reduce the effects of HFTs through design. IEX:
Has published its order matching rules
Refuses to pay for order flow
Charges fixed fees on large orders and a flat percentage rate on small ones.
Avoids colocation
Ensures market pricing data arrives at external points of presence (internet exchange points along your packet’s path) simultaneously.
IEX has even created a “Magic Shoebox”. Designed to slow down traffic coming in and going out of the exchange.
This box contains 61 km of fiber optic cable that’s designed to add a 350 microsecond delay. Essentially, creating a speed bump for all network traffic.
IEX is what’s called an alternative trading system (ATS). These ATSs exist outside of traditional securities markets. While they promise a solution to front-running HFT’s they have their own misgivings. Many have problems with insider trading and predatory behaviors, especially when trades are anonymous and have no specific order information before trades occur. These anonymous ATSs are called Dark Pools.
Dark Pools
Dark pools are private exchanges for trading securities. These exchanges are pools of liquidity not accessible by the investing public hence the name dark pool. They allow hedge funds and institutional investors to make privately negotiated trades, called “block trades”.
Some institutions use these pools to avoid large price impacts and can be broken up into smaller orders executed across various exchanges to hide trading activity (see more). See more about slippage and liquidity in our AMM (part I) edition.
Dark pools (categorized as “Alternative Trading Systems (ATSs)” by the SEC) allow large entities to trade anonymously, without revealing the order price nor size to other dark pool participants. These dark pools exclude HFT firms, providing a refuge from front-running.
However, Dark Pools need sufficient liquidity in order to execute trades at reasonable prices. In an effort to increase liquidity, they may give their own proprietary trading desks access to the markets.
Dark pools move the information from large national exchanges to private exchanges. While the information is different from traditional the exchange-to-exchange kind, the same arbitrage opportunities exist.
And while dark pools are supposed to protect traders from this kind of arbitrage, the opportunity is too profitable to ignore. Several dark pool operators have given their own trading desks information to improve their trades, front-running their customers. One dark pool operator’s compliance department warned them that this was illegal, and they did it anyway.
Another dark pool operator (Pipeline Trading Systems) was caught operating an undisclosed proprietary trading desk (division of the company that places trades) which composed the overwhelming majority of volume within the dark pool. Not only did their “Affiliates”—aka the Pipeline Trading desk—get information about trades, they also got better access to the system (colocation) and information about the Pipeline’s order-matching engine (the system’s rules) so they could more effectively front-run other dark pool subscribers.
Still yet another large dark pool operator gave HFT funds access to their pools with special order types, allowing them to get an unfair advantage over regular subscribers. They even let some preferred subscribers avoid trading against the HFT funds. The dark pool let HFT coyotes into the henhouse, armed these coyotes with forks and knives, and created a “VIP” section where special hens could order omelets and watch the mayhem below.
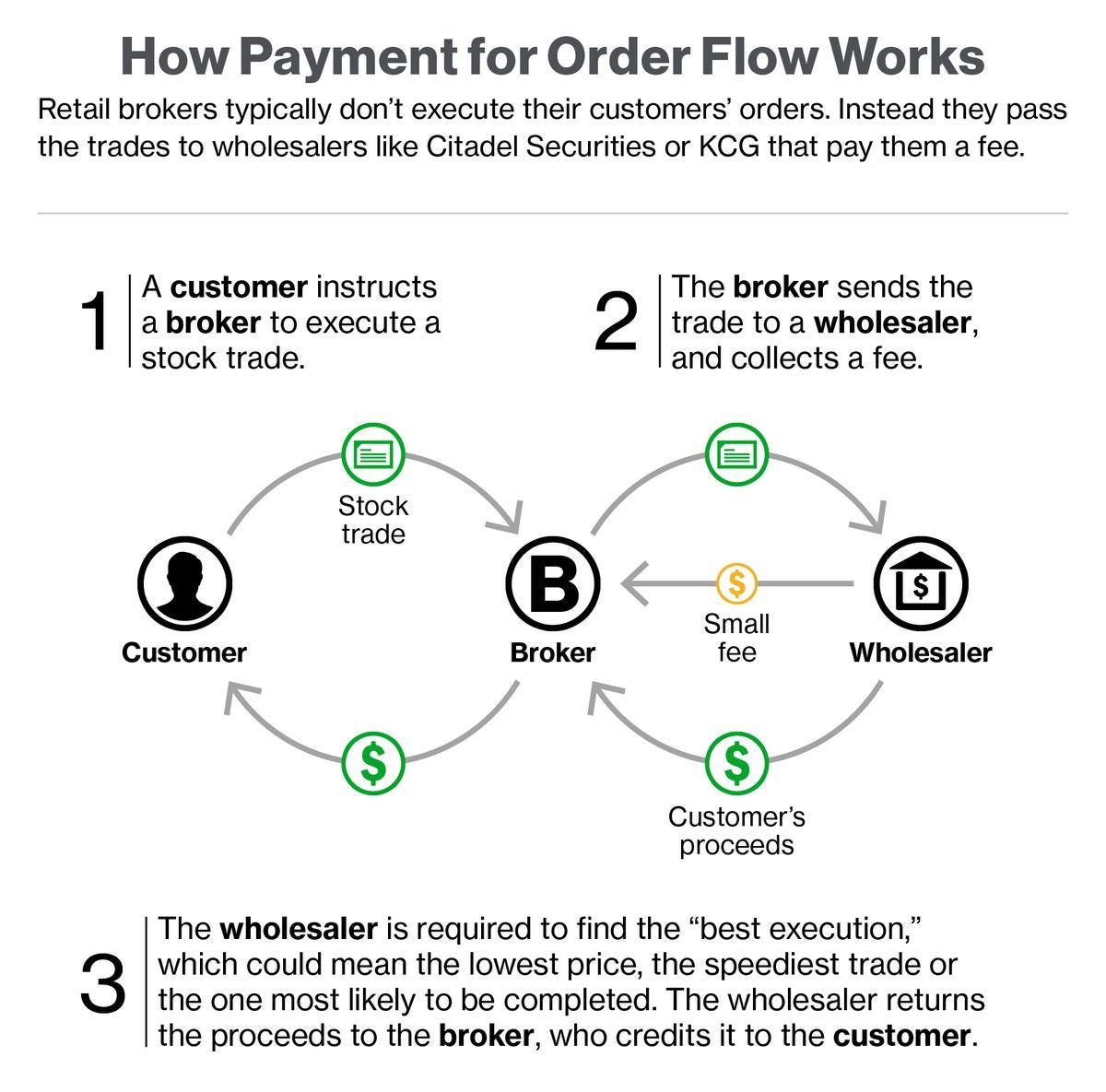
Payment for Order Flow
Payment for order flow is another way to capitalize on this price information. Market makers will pay Stockbrokers to route users’ trades to market makers for fulfillment. Robinhood made waves as one of the first broker-dealers to offer free trades and zero fees on account maintenance or any fund transfers. How do they afford to do this? Famously, the market maker Citadel Securities buys Robinhood’s order flow for $2.6 billion a year.
Bernie Madoff, infamous for running the largest ponzi scheme in history, said this of payment for order flow:
“[...] It was characterized as this bribe and kickback and something sinister, which was very easy to do. But if your girlfriend goes to buy stockings at a supermarket, the racks that display those stockings are usually paid for by the company that manufactured the stockings. Order flow is an issue that attracted a lot of attention but is grossly overrated.” -Bernie Madoff
Broker-dealers are obligated by law to provide a “best execution” price—no worse than the National Best Bid and Offer (NBBO)—to their customers, but these prices, notoriously, do not provide enough information for customers to verify them. Additionally, NBBO prices often go unrecorded, making it extremely difficult to determine whether traders got the right price or not.
Even if the prices are recorded, HFTs can take advantage of the latency between the NBBO’s calculation time and its publication. Because HFTs can access market information (prices) faster than the NBBO price can be published, HFTs will pre-calculate future NBBOs, front-run trades, and pocket a small but assured profit. Payment for order flow (PFOF) allows brokerages to share in some of these profits.
The SEC has said about PFOF:
“While the fierce competition brought on by increased multiple-listing produced immediate economic benefits to investors in the form of narrower quotes and effective spreads, by some measures these improvements have been muted with the spread of payment for order flow and internalization.”
MEV in Blockchains
All of these TradFi examples of arbitrage come from one thing: having access to information. Intuitively, buying low and selling high is not a new concept. It’s not always bad either. In fact, arbitrage is a crucial part of improving market efficiency.
It’s seen in traditional finance and in Amazon retailers. Amazon reselling has gained huge traction among Zoomers who purchase products in stores and then sell them on Amazon at marked up prices.
But crypto is speed-running the history of finance. MakerDAO created the first decentralized lending project in 2014, Uniswap launched in 2018, and Compound set web3 on fire with yield farming in 2020. With DeFi comes opportunity.
There’s a new kind of arbitrage in finance: Maximum Extractable Value (MEV). Formerly referred to as Miner Extractable Value, MEV includes DEX arbitrage, liquidations, and NFT sniping are possible through crypto-economic protocols like Ethereum—and it is very valuable. There are bots constantly searching for these opportunities throughout the mempool, but ultimately, the entity that has final control over these arbitrage opportunities is the block producer.
In proof of work systems, miners are the block producers, and in proof of stake systems, validators are the block producers. Because these entities produce the last set of transactions to finalize, they can add, remove, or replace transactions as they see fit without intervention from others. Only block producers can guarantee the execution of MEV transactions, so if they find an arbitrage opportunity, they can capture it. In web3, block producers have “god mode”.
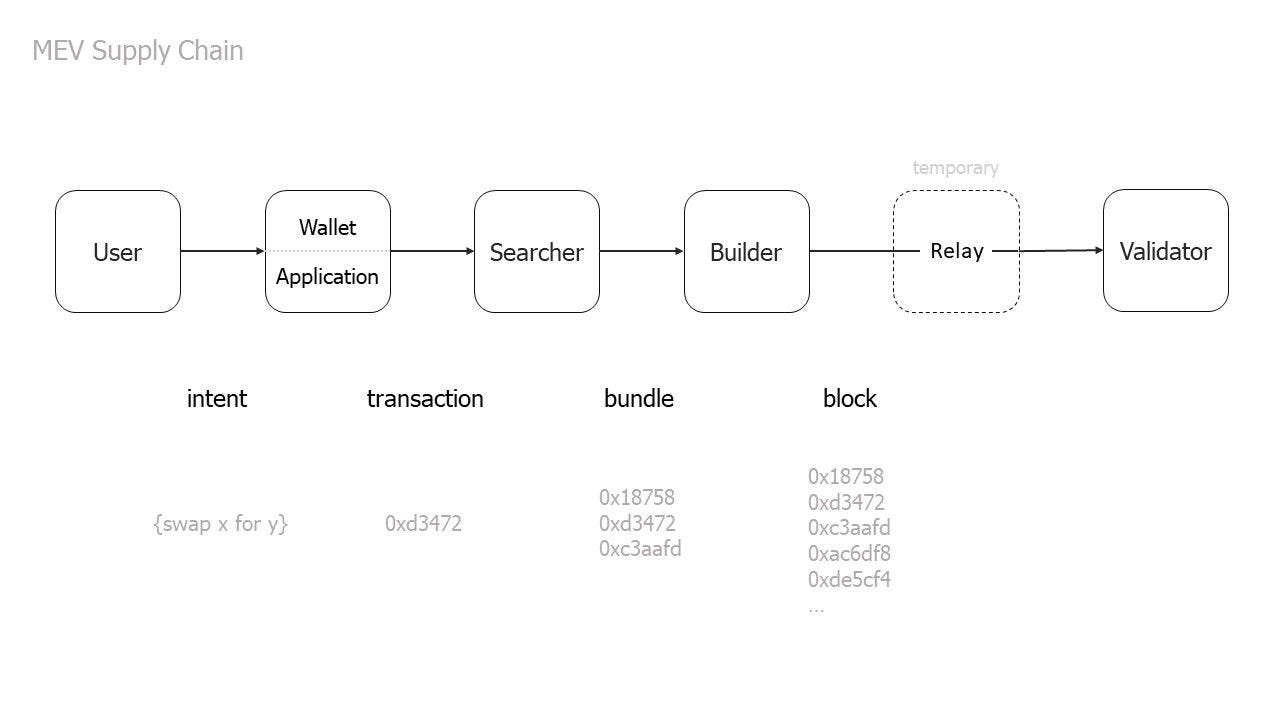
The MEV Supply Chain
Author: oxdog.eth
“The MEV Supply Chain describes the chain of activity which helps users transform intentions into finalized state transitions in the presence of MEV.” - Stephane Gosselin.
The MEV supply chain plays an essential role in the MEV landscape. Regardless of MEV mitigation techniques or ordering rules of transactions, the MEV supply chain exists in all blockchains. The players of the supply chain might look different on each blockchain, but the interaction between them is crucial because poor design can lead to a dystopian result.
Who are the MEV Supply Chain players, and what are their roles?
User
The start of the chain is always the user: anyone with the intention to interact with the chain, be it buying an NFT, swapping USDC for WETH on Uniswap, or taking out a loan on Aave.
Wallet / Application
Wallets are the interface connecting users to the blockchain. The Application Layer groups together dApp UIs and Smart Contract Protocols. Components work together to execute user intent.
On this layer, developers can make decisions on behalf of their users on how to deal with MEV. For example, a critical decision for wallets is whether the transactions are submitted to the public mempool or directly to a builder privately. The difference is that bots monitor the public mempools to identify MEV opportunities, as it’s where pending transactions usually reside. Private transactions fly under the radar of these bots because they skip the mempool and are directly submitted to a block builder. They protect users from being attacked directly by bots but don’t mitigate MEV, as the MEV extraction opportunity just gets pushed to the next block.
Searchers
Searchers are users that try to identify MEV opportunities by running complex algorithms, sorting through on-chain data and transaction pools, and operating bots. Their name comes from their “searching opportunities” task - hence the name searcher.
Even though their main goal is to extract the most profit for themselves, they play a vital part in the DeFi ecosystem by balancing markets and ensuring fast liquidations. But in dysfunctional MEV supply chains, searchers could extract a disproportionate amount compared to what they provide, leading to an MEV dystopia.
Builder
Builders aggregate transactions to construct a block.
Before the Merge, the role of building blocks and proposing them was handled by miners. After the Merge, the concept of Proposer Builder Separation (PBS) was put forth, allowing independent parties to fulfill each task. This enables block proposers to become lighter clients in the future to strengthen decentralization, as building blocks can be computationally heavy. In the current state, block proposers can still build blocks themselves, but once PBS gets implemented into the core Ethereum protocol—called enshrined PBS—this will no longer be possible, and the roles will be separated.
In Layers 2s, the sequencers play the builder role as they construct rollup payloads to submit to Layer 1.
Validator
Validators, aka Block Proposers, have consensus duties. They are the ones who propose, validate, and finalize blocks. As mentioned, they also had the role of building blocks and will continue to.
Relayers
Relayers are a temporary entity between proposers and builders. The problem that led to the need for relayers is that proposers can still build their blocks. Hence, when selecting a block from a builder, the proposer could reconstruct it and capture all MEV for themselves, cutting out the builder from the deal.
In short, Relayers prevent proposers from stealing MEV from builders.
The Relay MEV-Boost, built by Flashbots, takes the builders' blocks and verifies they are legitimate. They then present the blocks to the proposers by only showing the profitability of the block, not revealing the content. The proposer then picks the most profitable block, commits to proposing it, and the relayer sends the block content over so the proposer can submit it.
With enshrined PBS, Relayers will become obsolete as Block Proposers will not be able to build the blocks for themselves. Until then, this trusted party enables the cooperation of builders and proposers off-chain.
Example MEV Attacks
Author: oxdog.eth
Searchers have a variety of opportunities to extract MEV. There are two broad categories: Short-Tail (ST) MEV and Long-Tail (LT) MEV. ST MEV occurs frequently and is highly competitive. LT MEV, on the other hand, is a one-time opportunity like a DAO proposal that changes a protocol's parameters and creates the MEV as a result. We will look at the two most common ST MEV strategies - Arbitrage and Liquidations. We will also discover three techniques for how searchers place their transactions in a block to extract MEV.
Arbitrage
“Arbitrage is the simultaneous purchase and sale of the same asset in different markets in order to profit from differences in the asset's listed price.” - MEV Wiki.
Arbitrage exists in all markets; in crypto it’s the price difference between protocols where tokens can be swapped. This can be a Decentralized Exchange (DEX) like Uniswap, or protocols where you can mint one token for another (e.g. wrap ETH to stETH). The constant flow of transactions by users constantly causes shifts in prices that searchers can expose.
Arbitrage can come in many forms and sizes; essentially, it always takes advantage of price differences.
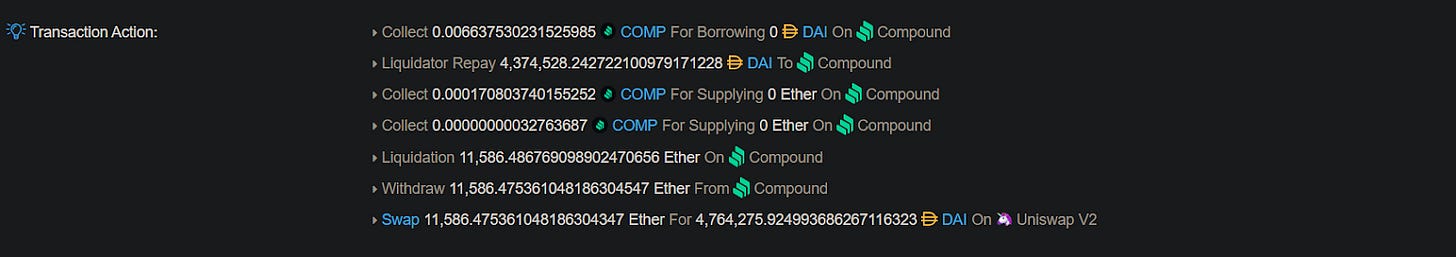
Liquidations
When taking out a loan on Aave, you need to supply collateral that can be taken from you if you cannot repay the loan. In DeFi, the loan collateral rate is very high. For example, if you don’t want to sell your ETH because you think it will go up but need $1000 USDC, you go to Aave and supply $2000 worth of ETH to take out the USDC. Unlucky you, you did this before the bear market started, and now your provided collateral is only worth $1200. This puts your collateral below the allowed threshold, and you can be liquidated by anyone.
This liquidation is often executed by searchers constantly watching all positions, trying to be the first to trigger a liquidation. Liquidations can often be quite profitable as searchers receive the hefty liquidation fee a borrower pays. Take this transaction, for example. It made $2.2 Million in Gross Profit by liquidating a loan on Compound.
From the Front to the Back to the Sandwich
Front- and Back-Running is not an MEV strategy like arbitraging; it describes how the searchers place the transactions in the block.
Back Running
Back running means the searcher places the transaction right after the one that exposes an MEV opportunity. For example, suppose someone swaps a large amount of USDC for ETH on Uniswap. In that case, it will cause a price shift between DEXs, allowing a searcher to place their transaction afterward to capture the arbitrage opportunity. Back running is harmless as it does not damage other network participants.
Front running
Front running means placing the transaction right before the targeted transactions. A widespread use case is generalized front-running bots that snipe profitable transactions of other users or bots. This works by monitoring pending transactions, copying profitable ones, and submitting them with a higher gas fee to ensure sooner inclusion. This approach became less effective with the introduction of Flashbots, as bots can now skip the mempool to fly under the radar of front-running bots.
Sandwiching
Sandwiching is front- and back-running combined. Their structure is “Searcher TX - User TX - Searcher TX,” hence the name Sandwich.
An example of a more notorious attack is sandwich attacking a DEX swap made by a user. Due to the self-balancing nature of DEXs, the price of the bought asset increases after the swap—the greater the exchanged amount, the greater the price increases. Sandwich traders take advantage of this by purchasing an asset for cheap before a large trade passes through and selling the asset afterward for a higher price. This increases the slippage of the targeted user leading to a loss.
A Peek into the Future of MEV
Author: Jake and Stake
MEV is the value that comes from information about economic activity. MEV can also be reframed as the value of information. Its value comes from having access to this information before anyone else or the ability to interact with it in privileged ways and benefit from it. MEV allows DeFi to function by improving market efficiency.
The power to order transactions is the source of MEV's value, and block producers have this power. They have the ability to add, remove, or reorder transactions to extract value that the system wasn’t designed to emit.
Front-running, back-running, and sandwich attacks are some examples of arbitrage techniques that target DEXs. These attacks are quickly becoming more sophisticated, including: NFT sniping, liquidations, and cross-domain arbitrage.
In traditional finance, order flow is the equivalent of “MEV”. High frequency trading is one example of MEV extraction. HFT firms can front-run, back-run, and sandwich attack user transactions that are routed through them. These firms invest heavily into reducing latency in order to capture this value, and co-location has become a lucrative business for exchanges, which charge HFT firms millions of dollars for the privilege of “low latency access.”
The Dark Side of MEV
Bot operators are constantly looking for opportunities, and they don’t care how these opportunities arise. A bot doesn’t have sympathy for a user that accidentally set a high slippage limit.
MEV can be extracted via:
Spam War: In this scenario, transactions are ordered randomly, which incentivizes bots to send thousands of transactions in order to capture the opportunity. Takes up a ton of block space, memory & compute resources, and crowding out typical use cases.
Latency War: Ordered transactions, first in first out (FIFO). Block builders (MEV searchers) are then incentivized to quickly send transactions to block producers. The closest block builders will be able to buy the block space fastest, causing a latency war. The most dominant block producers sell access to block builders which centralizes validators and block production.
Auction: Block construction is outsourced to 3rd parties, and block builders compete on price rather than latency. Efficient markets determine the dynamic between block production and MEV searchers. Flashbots is one such auction solution.
MEV Dystopia vs MEV Utopia
Dystopia
Colocation services create gatekeepers in block builders and MEV capturers. In this economic design, block builders and block proposers will combine forces, oversee transactions, and capture MEV. This has a centralizing effect because the more profitable this entity is, the more capital they can acquire to capture block rewards through mining or validating.
Eventually, this entity will create more validators and become so powerful that they can determine protocol rules and soft-fork the chain. Centralization like this is not Byzantine Fault tolerant and defeats the credible neutrality of blockchains.
This future will resemble traditional financial:
Centralized actors
Permissioned broker-dealers
Government induced monopolies
Utopia
Transactions are permissionless and censorship resistant with transparency of the MEV supply chain. The value that each actor extracts is visible and apparent to users.
Competition is used to determine market prices through proposer builder separation (more later), and block producers are extracting value in proportion to the amount of stake that they have in the network.
Flashbots and the Current State of MEV
Flashbots was created to prevent exclusive access to hash rate.
The “MEV Dystopia” describes a combined entity (composed of node operators and MEV searchers) that extracts value from transactions, splitting the profits. This creates a private market for block space and has a centralizing effect on block space. Actors that get these extra profits can reinvest them into:
More Nodes
Better MEV strategies
Alternatively, Flashbots creates a market for block producers to sell their block space for the greatest profit. Flashbots released MEV-Geth which is client software that allows Ethereum miners to accept transaction bundles from 3rd party block operators and include them into their block.
Post-Merge, Flashbots now lets validators use MEV-Boost to maximize their staking rewards by selling block space to block builders.
Chains without an MEV solution face problems like deep reorgs, spam, and concentrated block production.
If one party has enough money to buy another part of the MEV supply chain, they will. So the only way to protect the decentralization of the entire stack is to create sufficient competition at all layers.
MEV-Boost
MEV-Boost is a sidecar solution for validators to sell their block space, without being tied to a particular client. MEV-Boost is feature complete and in the testing stage.
The goal of MEV-Boost was to create a permissionless system where any validator could benefit from MEV.
In Ethereum POW, miners were incentivized to run MEV-Geth clients in order to capture the additional rewards from MEV. This led a large majority (90%) of miners to run the software, reducing client diversity. The majority of Ethereum POW nodes are Geth nodes. MEV-Boost works with “any Ethereum consensus client” promoting client diversity; Prysm, Lighthouse, Teku, etc.
Estimates from Flashbots say that 60% of total validator rewards will come from MEV.
Proposer-Builder Separation (PBS)
Block producers have a complete view of the content of MEV bundles, which gives them the option to front-run, censor, or otherwise extract value from them. Searchers must be careful regarding to whom they send these bundles.
Any average validator could take this value for themselves, leading MEV searchers to exit the auction system. Then, a similar market dynamic outlined in the MEV dystopia will materialize: MEV searchers and validators combine resources to outcompete other searchers and validators.
The MEV solution outlined using MEV-Geth doesn’t scale with the number of validators. The solution is to separate the responsibilities of validators into two roles: block “proposers” and block “builders”.
Block builders will accept bundles from MEV searchers, build entire blocks from these bundles, encrypt the blocks, and then send the blocks to validators. Validators cannot see the contents of the block. All they have to do is determine how much value the block contains and pick the block with the highest value.
Create a block builder role where they assemble bundles from MEV searchers into blocks who send these blocks to the block proposers (validators). Block builders bid on block space and validators will choose the block they want to add based on these bids (or among other factors).
⚠️ Note: There could still be centralization at the builder level.
This allows individual stakers to benefit from MEV. This shifts centralization to the ”Builder” layer, but it’s better to have centralization at that level than at the validator level. In any case, it gives us another opportunity to address the power law dynamics of MEV.
Enshrined PBS
Relayers
With MEV-Boost, “Relayers” receive blocks from block builders and submit them to validators for inclusion. Once Ethereum introduces PBS at the protocol level, the need for relayers goes away.
With most centralization risks comes censorship risks, however relayers don’t have an incentive to censor transactions. They leave money on the table if they do censor transactions. It should be noted that relayers can be coerced into transaction censorship by governments. Ideally, there is enough relayer diversity such that relayers not in that nation state can pick up those transactions. In turn, these relayers would be more profitable than the censoring ones and the subsequent validators.
In any case, enshrined PBS has a solution: crLists.
crLists
Enshrined PBS uses crLists to replace relayers. This scheme has block proposers create a list of transactions called the crList that have the correct nonce, sufficient balance, and sufficient priority fee and max fee.
Conclusion
At some level, centralization is going to be a force to contend with at all parts of the stack. Centralization is something of a law of the internet at this point. Anything with returns to scale and network effects will create natural monopolies.
The best we can do is introduce competition in order to create the best service, but if the best service is a centralized one, is that what we want? At some level, that kind of power and control can lead to censorship, which is what crypto stands against.
The Byzantine Generals Problem is a way to determine shared truth even if there are malicious actors in the game, and to prevent transaction censorship. At some level, decentralization is an insurance policy. We don’t necessarily need censorship resistance at all layers of the stack.
The need for censorship resistance on Instagram may not be as important as financial transactions.
Karma Case Study: The Tale of Oxbad
Author: Elemental
On September 27, 2022, a user attempted to swap approximately $1.85 million worth of cUSDC (Compound USDC) for standard USDC on Uniswap v2. Unfortunately, low liquidity for that trading pair resulted in extreme slippage, and they only received slightly more than $500 in USDC in the end. Devastating! Where did that value go? An MEV bot known as Oxbad recognized this as a massive arbitrage opportunity and conducted a sophisticated back-running scheme across several DEXs and protocols—reportedly netting around 800 ETH, or roughly $1.02 million, in profit. If the story ended here, it would be a powerful cautionary tale about the dangers of slippage and MEV in DeFi. But like Omar Little of The Wire, there are those in the crypto world who rob bad guys. One such bandit hacked Oxbad about an hour later, stealing not only the 800 ETH they arbed, but also all the additional ETH (in the form of WETH) in their wallet. This heist netted the hacker around 1100 WETH in total. Oof. Karma!@bertmiller from Flashbots breaks down the play-by-play details in this thread:

But wait, there’s more!
After discovering the hack, 0xbad contacted the hacker through transaction input data to try to recover the plundered booty. Their appeal is an odd mixture of aw-shucks congratulations, businesslike negotiation, and hollow threats.
“Congratulations on this, we got careless and you sure managed to get us good, that was not easy to see. We would like this cooperate with you on resolving this matter. Return the funds to 0x19603D249DF53d8b1650c762c4dF31f013Dce840 before September 28 at 23:59 GMT and we will consider this a whitehat, we will give you 20% of the retrieved amount as a bug bounty, payable as you see fit. Should the funds not be returned by then, we will have no choice but to pursue accordingly with everything in our power with the appropriate authorities to retrieve our funds.”
“Appropriate authorities” is a delightful bit of bluster. Two hours later came the counterproposal:
“What about normal people who you have mev'ed and literally fucked them? Will you return them? Return the funds to all people before September 28 at 23:59 GMT and we will consider this a whitehat, we will give you 1% of the retrieved amount as a good heart sign, payable as you see fit. Should the funds not be returned by then, we will have no choice but to pursue accordingly with everything in our power with the appropriate authorities to retrieve our funds.”
Well not “literally”, but the gist of the response is clear. While no one is shedding any tears for 0xbad, it’s important to remember the original user who still lost their (presumably legitimately owned) $1.85 million worth of cUSDC. The ultimate lesson from this tale is how crucial it is to understand liquidity, slippage, and MEV if you plan to use any of your hard-earned funds in DeFi. Which is why the DeFi Download is here.
MEV Dashboards
Actions steps
📖 Read MEV-Boost in a Nutshell | Flashbots
⛏️ Dig into The MEV Supply Chain | Stephane Gosselin
🎧 Listen Crypto’s Existential Threat | BanklessHQ
🎧 Listen Why You Can't Afford to Ignore MEV | (Hasu & Stephane Gosselin)
Tokenomics 101: Burning Tokens
Author: Kornekt
The future of every crypto token depends on the management of its economics. The basic principles of supply and demand determine price, token economics (tokenomics) is the plan of developers to stabilize and increase their token's value. Among other factors, token supply is an important element in tokenomics when capturing protocol value.
In this edition of Tokenomics 101, we are looking into the token supply and burn mechanisms of two exciting web3 projects: MakerDAO and CultDAO. What are the methods in use at these organizations to increase the value of their tokens and attract more buying pressure? Let's find out!
MakerDAO
MakerDAO is a DeFi lending protocol on Ethereum. The protocol uses three tokens—Maker(MKR), Dai(DAI), and collateral tokens—to facilitate peer-to-peer borrowing and lending. Maker is the native token of the MakerDAO ecosystem and Dai is a stablecoin pegged to the US dollar offered by the protocol.
The Maker token is a lever that helps keep the value of DAI stable. It is an ERC-20 token that works as MakerDAO's governance token, is used for payment of loan fees, and serves as a recapitalization source for loans. The Maker lending protocol uses crypto collateral, so there must be a means to ensure that the price variation of the crypto market does not affect the DAI dollar peg. This is where MKR comes in. When the peg fluctuates, the system either mints or burns MKR to keep DAI stable at $1.
Here's how it works: if the price of ETH changes and the protocol's debt exceeds a certain limit, the system will mint new MKR tokens and then auction them for DAI to pay the deficit. On the other hand, when the system runs beyond a certain surplus threshold, the extra DAI is used to buy MKR back and subsequently burn it.
The Maker token is also burned using the loan fees borrowers pay. When borrowers repay their loans, they also pay stability fees denominated in DAI. The system uses this fee to buy back MKR which is then burned. This means MKR will continually be burned as long as people request loans on the system.
At inception, the Maker Protocol launched with 1,000,000 MKR tokens. However, there is no limit to the number of MKR tokens that can be minted; it all depends on whether the system runs on a surplus or a deficit. Nevertheless, if the system is governed well, it is expected that the number of Maker tokens will gradually reduce as it is burned using excess DAI. As of October 24, 2022, the total supply stands at 977,631 MKR, meaning that 22,369 MKR has been burned so far.
CultDAO
CultDAO is a decentralized autonomous organization on a mission to foster the growth of decentralization by funding blockchain-based projects. The DAO is a decentralized venture capital that aims to speed up the DeFi revolution. It uses its native token called CULT to both drive governance in the DAO and to carry out its funding mechanism.
The Cult token has a max supply of 6,667 billion CULT and employs certain burn mechanisms to make the token deflationary. For every transaction using CULT, 0.4% of the transaction amount is charged as a fee and goes into the CULT treasury. When the treasury has accumulated up to 15.5 ETH worth of CULT, it sends 13 ETH to the wallet of any of the investee proposals that have been approved for funding. The remaining 2.5 ETH goes to a burn wallet. This means that for every 60,000 CULT tokens raised, 10,000 are burned.

Since the DAO is more like a Venture Capital (VC) fund, it receives a certain percentage of the investee project’s token in return for its investment. The DAO requires the investee to exchange this percentage of their token into CULT and send 50% to a burn wallet. This burn further cuts the supply of the CULT token. The other 50% goes to holders of dCULT (dCULT is the proof of stake token CULT holders receive when they stake their tokens).
That said, the more the value of CULT declines against ETH, the more CULT is burned. More of the tokens are also taken out of circulation and placed in the treasury. This mechanism is in place to help the token scale through long crypto winters and ensure fast recovery at the onset of bull markets.
Security Scares: Mango Markets Manipulation
Author: Austin Foss
October has been a record breaking month for DeFi hacks and exploits according to Chainalysis.
Not one, but two incidents occured where more than 100 million USD worth of cryptocurrencies was compromised. In the first week of October, Binance halted "deposits and withdrawals via the BNB Smart Chain" because an attacker hacked the Binance Bridge for approximately 566 million USD worth of BNB. They are still on the run and got an estimated 100 million USD worth of tokens to other chains before the bridge was halted.
Not even a week later, on October 11, a DeFi protocol operating on Solana, called Mango Markets, was completely drained of all deposits worth approximately 100 million USD. Although both attacks compromised similar total token values the nature of the Mango Markets attack highlights some subjectivity of a mantra within the blockchain ecosystem; code is law.
Exploited
While the Binance attack was the result of a bug in the bridge's code, the Mango attack was executed by using the protocol as it was intended to be used and sophisticated token price manipulation.
By taking an outsized position of Mango Markets token's perpetual contract the MNGO price experienced a 5-10x price increase. Using their now highly profitable long position the attacker borrowed the maximum value allowed, completely draining the protocol of all user deposits and causing the Mango team to freeze the protocol.
Negotiations
Following the incident the attacker submitted a proposal to the DAO for a vote titled "Repay bad debt", and then themselves used their nearly 33 million MNGO tokens to vote yes.
This proposal is no longer visible from the voting page but multiple comments from Mango Markets' users sharing how they have individually been affected are still present. Some voters added to the 'yays' but nearly 10 times more 'nay' votes were cast, 313 million MNGO against.
A counter offer was later proposed and passed on October 15. Although the attacker doesn't appear to have voted in favor of the proposal, by the wording, "the amount you have agreed to return", implies that the terms were agreed upon prior to being submitted to the DAO for a vote, resulting in 473 million MNGO in favor of this resolution. At the end of this proposal the Mango Markets DAO agreed to "not pursue any criminal investigations or freezing of funds once the tokens are sent back..." which the attacker paid back.

Subsequent votes took place deciding on the most equitable distribution procedure to make users whole. Mango Markets as a protocol remains unusable, but if you were a victim of this attack there is currently a recovery page available.
Did the Attacker Do Nothing Wrong?
It wasn't long before the identity of the attacker began to be suspected. Within 24 hours it was known that whoever was behind this had withdrawn 7.5 million USDC to the ponzishorter.eth address.
About a half hour after the attacker started returning the aforementioned funds, and was already in the clear legally, did the attacker confirm his identity as Avraham Eisenberg. Curiously this is not the first time Avraham has done something like this. Early this year he was accused of rugging a project he was a developer for, FortressDAO.
Regardless of whether his first exploit used a different DeFi mechanism, both the FortressDAO and Mango Markets attacks executed by Avraham were perfectly within the bounds of the smart contract code. No social engineering attack, no vulnerability from a lapse in a validity check; for all intents and purposes the code worked as intended.
Is Code Law?
Even though the code worked as intended, it seems intuitively implicit, especially to the victims, that this was not the protocol working as intended. Whether Avraham thinks what he did was wrong or not, only returning 67 million USD worth of the funds, he was still wary enough of legal action to ask for amnesty during negotiations to avoid any social enforcement by the DAO.
Market manipulation would be the way to pursuing what he did, but even pursuing that option what jurisdiction would this fall under? Thankfully the users who lost funds are able to get some compensation but this might not always be the case.
If code is not law how would, and should, an exploiter be held accountable?
Project Releases 🎉
Hand-picked articles to understand the current state of the DeFi ecosystem
Scroll announces upgraded zkEVM testnet
Deploy contracts using existing L1 tools like Hardhat and Foundry
ERC-20, ERC-721, and ERC-1155 standards are now all supported on Scroll
Developers must be approved by the Scroll team before deploying contracts to this testnet. Register here:
https://signup.scroll.io/

Offchain Labs of Arbitrum acquires Prysmatic Labs of Prysm
Prysm is the most popular consensus layer client software with 40% of Ethereum nodes using it
Arbitrum One is the L2 with the most TVL at $2.58B
First acquisition of an Ethereum client team in history
Could hint at a new exit model for client teams (acquisition)
Arbitrum announced that they would keep Prysm fully open source


zkSync launches L3 testnet “Pathfinder”
zkSync envisions an ecosystem of customizable blockchains (“HyperChains”) powered by the zkEVM.
zkSync will allow developers to choose from 3 data availability options
ZK rollup — Choose this if you want to have the full security of Ethereum (Good for DeFi).
zkPorter — Choose this if you want a mixture of your data to be made on-chain and off-chain to optimize for cheap, fast, and secure (good for gaming).
Validium — Choose this if you want ultimate performance with slightly less security than Ethereum (Limitless Use Cases).
Customizable privacy, tokenomics, and native “HyperBridges”.

Polygon launches zkEVM testnet
Supermodular.xyz launches
A venture fund for digital public goods
Formerly Gitcoin Holdings
Roadmap includes:
https://pluriverse.wtf/
and
https://hypercerts.xyz/

Across Protocol airdrop is live
You can qualify if you were:
An early bridge user - Used the bridge before July 19, 2022.
A community member - Made significant contributions in the community.
An LP provider for $ETH, $USDC, $WBTC and $DAI into Across.
Even if you haven’t used Across yet, your address may have been selected to be eligible for the airdrop.


Nethermind has successfully transpiled UniswapV3 to Cairo
Minor changes were made to the Solidity source code to translate it into Cairo
Warp is a Solidity to Cairo transpiler that now supports the following:
abi.encode, abi.encodePacked
abi.decode - For now, only value types are supported
StarkWare and Nethermind have a joint partnership dating back to July 2021
https://cointelegraph.com/news/decentralized-exchange-uniswap-v3-gets-warp-ed-onto-starknet
https://medium.com/nethermind-eth/introducing-unistark-uniswap-only-warped-to-starknet-6b62d3a96690


Google search supports blockchain address lookups
Searching for Ethereum addresses returns information from etherscan
New blockchain Aptos released
Built on Move, a programming language based on Rust
Transaction pre-execution and expiration time.
Parallel smart contract execution
The total supply of Aptos is 1,000,739,234.25, however, 821,111,362.91 is currently staked
https://medium.com/aptoslabs/aptos-autumn-is-here-92a8d904eb49
Warning: There was no public sale



zkSync releases zkEVM and ZK Prover on public testnet
ZK proofs can be proved by a GPU
Uniswap community has voted to deploy Uniswap v3 to zkSync
Proof generation, aggregation, and on-chain verification

Roofstock Onchain sells first property via NFTs
Roofstock is a digital real estate investing platform for the single-family rental home sector.
Each home is titled in a limited liability company whose ownership is associated with a unique Home onChain, which is an NFT on the Ethereum blockchain
Each Home onChain is transferred using smart contracts, which are deployed on the Ethereum network, and the entire transaction takes place transparently on the blockchain
Purchase properties more efficiently and transparently with lower costs, compared to conventional residential real estate transactions
Buyers can seek a loan for up to 80% loan-to-value of the sale price of the NFT with USDC Homes, a DeFi lending pool maintained on the Teller Protocol.


Chirping Birds 🐤
🔥 and 🧊 tweets from across the DeFi ecosystem
























🛠 BANK Utility (BanklessDAO token)
With over 5,000 holders, BANK is one of the most widely held social tokens in crypto. So it bears asking, where are the best places to put our BANK to use? The five protocols below will allow you to deposit BANK in a liquidity pool and earn rewards. To get going, just click on the name, connect to the app, filter by BANK, and start earning passive income.


⚖️ Balancer
Balancer has two 80/20 liquidity pools, meaning that you are required to deposit 80% BANK and 20% ETH in the pool. There is one pool on Ethereum and another on Polygon. Once you’ve provided liquidity, you’ll receive LP tokens. Keep an eye out for opportunities to stake these LP tokens. There is nearly 500,000 USD in the two Balancer liquidity pools.
🍣 SushiSwap
SushiSwap has a 50/50 BANK/ETH pool. As with Balancer, you will receive LP tokens, and while you can’t stake them on SushiSwap’s Onsen Farm yet, you may be able to in the future. Liquidity providers earn a .25% fee on all trades proportional to their pool share. The SushiSwap pool has a little over 100,000 USD in liquidity.
⏛ Rari Fuse Pool- Deprecated Soon
This will be deprecated soon. The Rari Fuse Pool allows you to borrow against your BANK or earn huge APY by providing assets like DAI to the pool. At present, all borrowing is paused for this pool. There is over 450,000 USD deposited in the Pool
🦄 Uniswap
The Uniswap V3 liquidity pool is 50/50 BANK/ETH, and provides a price oracle for the Rari Fuse Pool. By depositing in the Uniswap pool, you can earn fees and help enable borrowing on Rari. This pool currently has over 500,000 USD in liquidity.
🪐 Arrakis
You can also provide liquidity to the Arrakis Uniswap V3 pool. The ratio is about 2/1 BANK/ETH. This pool is new, and only has a bit more than $6,000 in liquidity. In the future, you may be able to stake your BANK/ETH LP tokens within the protocol to earn additional rewards.
Get Plugged In
Event Highlights
ETH San Francisco—San Francisco California—Hailed as the West Coast’s premier Ethereum event of 2022, ETH San Francisco unites blockchain and crypto enthusiasts, as well as developers, industry experts, and tech companies. Discover more Ethereum events around the world here and check out the ETHGlobal site to get more updates about this and other upcoming events. November 3-5, 2022, San Francisco, USA.
🧳 Job Opportunities
Get a job in crypto! Do you like solving hard problems, care about building more efficient markets for everybody, and want to work at the frontier of decentralized finance? Rook is looking for full time contributors, with salaries ranging from $169,000-$722,000. There are positions ranging from engineering, recruiting, product marketing, copywriting, and design. Sound interesting? Sign up for our referral program and go full-time DAO.
Sr. Copywriter (❌ technical)
2D Graphic Designer
Quantitative Analyst