The AMM Edition (Part II) | DeFi Download
Your Trusted Source for 101s, Project Announcements, and Tokenomics Tutorials.
Dear Bankless Nation 🏴,
In the last issue of the DeFi Download, The AMM Edition Part I, we covered the basics of decentralized exchanges and Automated Market Makers. DEXs and AMMs are arguably what make DeFi as we know it possible, allowing for permissionless trading of digital assets and endless yield-earning opportunities.
In this AMM Edition Part II, we’ll go from the 101 to 201, starting off with DEX Aggregators, which enable users to take advantage of search-engine-like functionality to get the best deals on swaps. It’s like Expedia for your crypto journey.
We’ll also learn about AMM Bridges, which enable you to swap tokens across chains, and concentrated liquidity, which is the concept behind Uniswap v3 and Curve v2. Concentrated liquidity enables users to provide liquidity at the range in which there is more market activity. As you’ll see, concentrated liquidity creates increased capital efficiency and a higher rate of return for liquidity providers.
If you’ve always read about MEV but have no idea what Maximal Extractable Value really is or why it’s important, you will after this issue, which goes deep on MEV and Rook, a protocol that aims to give MEV back to the people. And if you’ve heard of Curve but always wondered about Convex, wonder no more. We round out this intermediate-level content with a great breakdown of veTokens vs “valueless governance tokens”, two security scares you should know about (Slope/Solana & Curve), and finish off with a handful of more advanced DeFi tactics.
After reading the AMM Edition Parts I and II, you should have an excellent grasp of many of the pillars of DeFi. Stay tuned to future issues of the DeFi Download for additional ways you can put this new knowledge to use. Thank you for being on this journey with us - onward to the Merge (which we’ll cover in depth during the next three editions of the DeFi Download!).
Contributors: BanklessDAO Writers Guild (Ap0ll0517, Austin Foss, d0wnlore, Elemental, helloashpreet, Hiro Kennelly, Kris, oxdog, siddhearta, Zero Mass, Jake and Stake)

This is the official newsletter of BanklessDAO. To unsubscribe, edit your settings.
🙏 Thanks to our Sponsor

The DeFi Download Guide to AMMs (Part II)

First we begin with some advanced concepts: DEX aggregators, Concentrated Liquidity, AMM bridges, and MEV. Afterwards, we break down a few of the AMM projects in the space. Part II of the DeFi Download Guide to AMMs will get you up to speed on the cutting edge of AMMs.
DEX Aggregators—The Search Engines of DeFi
Author: oxdog
When you want to swap your tokens, you have countless DeFi Exchanges (DEX) to choose from. Be it Uniswap or TraderJoe, dYdx or Curve. All exchanges have ever-changing swap prices and varying slippages. With over 214 DEXs listed on Coingecko, you will never get the best possible conditions relying only on your DEX of choice. But searching all DEXs for the best price is unreasonable, and you also don’t need to. This is precisely what DEX Aggregators are built for. They are a search engine of decentralized exchanges to find you the best conditions across all DeFi. What are they, how do they work, and what are the best aggregators?
What are DEX Aggregators
You can compare DEX Aggregators to search engines for hotels. When you search for a hotel to stay in, you have hundreds of options to choose from. If you are a maniac, you will visit every hotel’s website individually and compare their prices. If you are an ordinary person, you use a hotel search engine like Trivago that helps you find the best fit. It saves you time and money!
When you visit the same DEX over and over, it is like staying at the same hotel every time you travel. It is convenient, yet you are very likely missing out on lower prices and more beautiful stays. DEX Aggregators are here to help.
Decentralized finance is built on liquidity that users provide. The swap rate and slippage on these exchanges are determined by a formula that calculates it based on the underlying liquidity available. Because liquidity is constantly changing, prices fluctuate with it. DEX Aggregators monitor several liquidity sources across DeFi and use sophisticated algorithms to detect the most favorable rates with the least slippage.
When you trade on an aggregator, you are still using the underlying protocols of the DEXes, but the aggregator decides which one is the best for you. They can even split your trade across multiple exchanges to give you even better conditions.

Two famous examples for Dex Aggregators are 1inch and Paraswap.
1inch
1inch is the #1 Dex Aggregator with over $236B+ in total volume, 265 liquidity sources, and available on nine chains (Ethereum, Binance Chain, Polygon, Optimism, Arbitrum, Gnosis, Avalanche, Fantom, Klaytn). The aggregator can also be used for yield farming and has its gas token named Chi, which can be burnt on trade to save gas.
1inch also has a mobile wallet (ios/android) where you can store your assets, buy crypto with fiat, transfer on multiple networks, swap tokens, and stake 1inch to gain governance rights and eventually be eligible for gas refunds. You can find more 1inch stats here.
Paraswap
Paraswap is similar to 1inch, yet not as large with a total volume of $30B and is deployed to six chains (Ethereum, Polygon, Binance Chain, Avalanche, Fantom, Arbitrum).
A benefit of trading on Paraswap is the gas refund program. When you stake a certain amount of PSP, you can enjoy up to a 100% gas refund. For example, if you stake 5,000 PSP, which equals around $100 at $0,023 per token, you get 50% of your gas refunded.
Also, Paraswap recently opened early access to their mobile app. Currently, it is only available for ios users, and you have to stake PSP to be eligible. If you are curious, you find more information here and stats about Paraswap here.
More Options
Besides 1inch and Paraswap, you have other options you can trade on.
Lookout
In the future, it will be uncommon to visit a DEX or aggregator directly. As wallets' functionality and user experience improve, DEX Aggregators will be built directly into them. So instead of opening your browser, visiting an aggregator, connecting your wallet, and initiating a transaction, you can hit a swap button in your wallet app, which uses an aggregator under the hood.
Many wallets already have this implemented. For example, if you’ve ever used the swap feature on Metamask, then you used an aggregator since Metamask implements the same 0x API that Matcha uses.
If you haven’t tried a DEX Aggregator, now is your time. It will immediately pay off by saving money that would otherwise be lost on every trade you make.
AMM Bridges
Author: Elemental
A growing number of protocols and tools are building AMM-style functions to increase the speed and ease of bridging assets between different blockchains and rollups. Protocols such as Hop, Swim, and Synapse combine a mint-and-burn approach with AMM liquidity pools to enable fast and trust-less bridging between chains or rollups.


Mint & Burn
Let’s examine how this works using an example of bridging 1 ETH from Ethereum mainnet to Optimism. Starting with the basics:
A user exchanges 1 ETH for the protocol’s specialized synthetic bridge token (1 hETH in the case of Hop).
The “canonical token” 1 ETH is essentially held in escrow by the bridge contract.
The user’s 1 hETH on Ethereum L1 is sent to the bridge smart contact and burned.
A matching amount of bridge tokens (1 hETH) are minted by the protocol on Optimism.
The 1 hETH is exchanged for canonical 1 ETH (minus bridge fees) on Optimism.
AMM Pools
Of course, at times when demand for a token is higher on one chain or rollup compared to another, the supply of available canonical tokens could get out of balance or dry up. This is where AMM features come in.
AMM-style bridges create liquidity pools on each side of the bridge to maintain an ample supply of tokens in both directions. The protocols give liquidity providers a portion of the bridge fees as the incentive for depositing tokens in the pools.
As withdrawals and deposits change the composition of the pools, arbitrageurs take advantage of the price differences between the canonical and bridge tokens and rebalance the pools—the same way that do with liquidity pools on AMM exchanges.
Combo-Aggregators
While not actually AMM bridges, tools such as Zapper and Zerion make it easier to swap and bridge tokens at the same time using a single intuitive interface—greatly simplifying the process of exchanging tokens on one chain for different tokens on another chain.
Behind the scenes, they combine the functions of both an DEX aggregator and a bridge aggregator, routing the transaction between multiple DEXs and across at least one cross-chain bridge (which may or may not be an AMM bridge) to optimize the transaction. While these tools make transactions simple and automated, you’ll still incur the same transaction costs, risks, and time delays that would be involved with using the bridges and DEXs manually.
Concentrated Liquidity
Author: siddhearta
Uniswap V3 introduced the concept of concentrated liquidity in order to create capital efficient markets. Concentrated liquidity allows LPs to set the price range in which they would provide liquidity, so rather than their capital being spread thin across the entire constant price formula curve, it can be directed to a narrower range of prices where there is more market activity. Concentrated liquidity also makes capital more efficient by providing more fees to LPs as well as increasing market depth.


The introduction of concentrated liquidity allowed Uniswap to become the most flexible and efficient AMM ever and it also solved some of the problems that earlier liquidity pools created.
Low liquidity leads to slippage.
Low yield for liquidity providers causes them to move their assets elsewhere.
Concentrated Liquidity Creates More Market Depth
Market depth is a measure of how deep the liquidity pools are for assets traded on a DEX. A deep liquidity pool not only supports larger transaction amounts, but also higher transaction volumes. Pools that have low liquidity or market depth end up either not executing or having high slippage, where the expected price of a trade is significantly different than the price at which it was executed.
Concentrated liquidity provides greater depth because the assets liquidity providers allocate to the pools are concentrated within a narrow price range, rather than being spread out over the entire price curve. This means that concentrated liquidity creates more efficient capital markets and a better user experience because orders are executed more reliably and with less slippage.
Research has shown that by using this design, Uniswap V3 has been able to create deeper liquidity than many centralized exchanges. This means that not only are DEXs optimized for permissionless trading, but for larger trades, they offer price advantages compared to centralized exchanges.
Alternatively, in order to create the same depth of liquidity as Uniswap V2, LPs need to allocate far less capital, meaning that their remaining capital can be distributed to other investments.
Yield Farmers Want to Put Their Capital to Work
In order to create liquid markets, DEXs incentivize liquidity providers to deposit assets into pools in exchange for a percentage of the trading fees.
Liquidity providers are investors that have capital that they want to work for them, so they seek out yield generating opportunities. Yield farmers are investors who use DeFi to maximize their returns on their investments, often moving from protocol to protocol in search of higher yields.
Using concentrated liquidity, your money works harder for you.
Concentrated liquidity on Uniswap V3 opens up several advantages for LPs:
Increased capital efficiency: By focusing liquidity on a narrow price range, LPs can create sufficient market depth with less of an investment, thus allowing them to increase their exposure to other assets and reduce their risk.
Higher returns on capital: Due to the increased capital efficiency, LPs can earn a higher yield on their investments. Research has shown that Uniswap V3 outperforms V2 by an average of 54%. A higher return on capital means that yield farmers are less likely to pull their capital for other yield farming opportunities.
Multiple fee tiers: V3 introduced multiple fee tiers based on varying degrees of risk: 0.05%, 0.3%, and 1%. The 0.05% fee tier is for lower volatility assets, while the higher fee tiers are more volatile and thus higher risk.
A Word on Impermanent Loss
When liquidity providers put their capital into liquidity pools they are at risk of impermanent loss. Liquidity providers experience impermanent loss when the tokens they deposited into a pool lose value due to price volatility.
The risk of impermanent loss is offset by the yield generated by the liquidity pool, so it would seem that pools that have a higher yield have less risk of impermanent loss. When Uniswap V3 first came out, many people believed that because they were more capital efficient and had higher returns that the risk of impermanent loss was also reduced, but that is not the case.
Due to concentrated liquidity there is a greater risk of impermanent loss due to extreme price fluctuations. Providing liquidity to Uniswap V3 requires that LPs actively manage their positions to avoid impermanent loss.
In the early days of DeFi, retail traders could put their assets to work for them by generating yield in liquidity pools. As the Uniswap protocol has developed and become more capital efficient, it has also made it more difficult for retail traders to participate in providing liquidity.
MEV and Arbitrage
Author: oxdog
MEV stands for Maximal (or Maximum) Extractable Value and is an essential part of the crypto ecosystem. It is not only a source of profit but acts as an invisible hand that keeps systems in balance. Let’s dive into what it is, who uses it, its different types, and its good and bad sides.
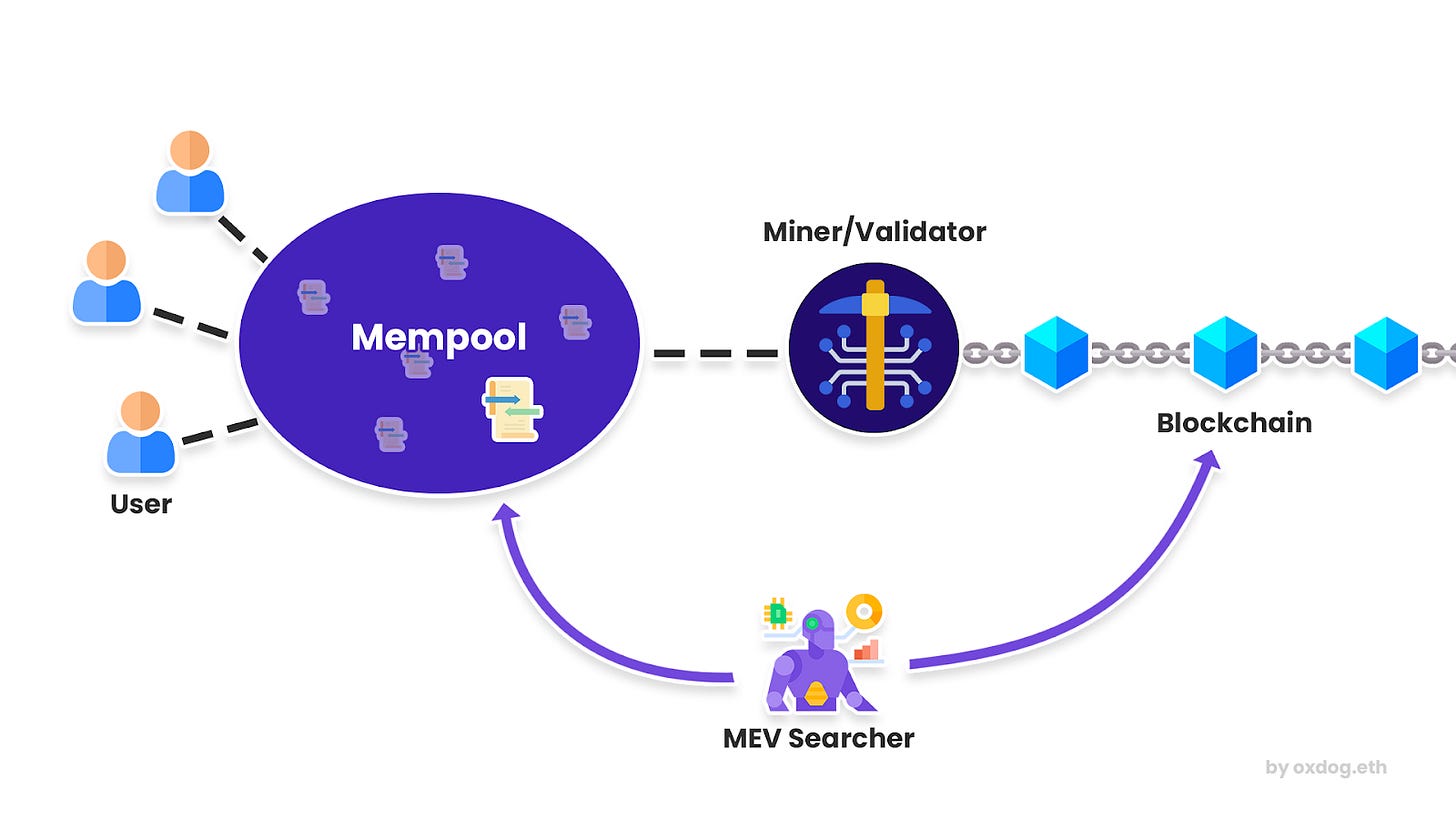
Within a block, economic energy flows into the blockchain through all incoming transactions. MEV Extraction is harvesting this energy for monetary gain by re-ordering, including, and excluding transactions.
In theory, the only actors capable of this are block producers (miners/validators), so one might suspect these are the entities getting MEV. (For simplicity, we will refer to miners and validators just as “miners”). In reality, the majority of opportunities are leveraged by other network participants—so-called MEV Searchers. MEV Searchers go through heaps of data looking for a profitable transaction—hence the name—and run bots that automatically execute them. This is also beneficial for miners because they get a profit share through higher gas fees usually paid by the searcher to ensure their inclusion in the next block. To become a searcher, you need to be technically savvy, know how to code, and be willing to tackle the intense competition.
But where do searchers find MEV opportunities? The answer is via on-chain data and the mempool.
The mempool is where all incoming transactions reside, waiting to be picked up by a miner to be included in the next block. Because this pool is public, searchers monitor it to detect transactions that might lead to profit.
On-chain data is also public and can also be analyzed to find opportunities. For example, searchers can monitor ETH’s price on decentralized exchanges (DEXs).
There is a vast range of different MEV types. We will have an overview on
Arbitrage
Liquidations
Front and Back Running
Sandwich Trading
Arbitrage
Arbitrage is taking advantage of price differences to make a profit. This tactic is quite simple and well known, hence very competitive.
A common place to practice arbitrage in crypto are DEXs. In essence, searchers monitor the prices and execute a trade when they can buy an asset to sell it on another DEX at a higher price. For example, a direct arbitrage trade would be buying ETH on Uniswap for 2.000$ and selling it on Sushiswap for 2.057$.
It is also possible to trade through another pair to make a profit. For example, USDC → ETH → DAI → USDC. This is called Cyclic Arbitrage and can become more complex with more pairs you trade.
To gain an advantage over competitors, it is possible to look for incoming trades in the mempool to determine if an arbitrage opportunity occurs after the trade and directly place a transaction to extract it.
Liquidations
Lending protocols require a borrower to over-collateralize their loan, which means their borrowed amount needs to be lower than a certain percentage of their collateral. For example, if a protocol allows for 50%, you can borrow up to $5k with $10k as collateral (e.g., 5 ETH at $2k to borrow up to $5k USDC). If the price of ETH fluctuates, so does your collateral's value. If the borrowed amount is greater than the percentage, the protocol allows the loan to be liquidated, which means the collateral gets sold to repay the lenders.
This is an excellent source of income for searchers as they receive the hefty liquidation fee a borrower pays.
Front-Running
Front running can be done by monitoring the mempool for a profitable transaction, copying it, and submitting it as their own with a higher gas fee to ensure sooner inclusion in the following block to steal the profit.
A widespread use case is generalized front-running bots that snipe profitable transactions of other users or bots. This approach became less effective with the introduction of Flashbots, as searchers can now skip the mempool to fly under the radar of those bots.
Back-Running
Back-Running is similar to front-running, but instead of stealing the profit, it takes advantage of the MEV caused by a successful transaction. For example, a swap on Uniswap will cause a price difference to Sushiswap, allowing a bot to place its trade after capturing the arbitrage. This approach is harmless as it does not damage other network participants.
Sandwich Attacks
A Sandwich attack is a combination of front- and back-running and counts among the more notorious attacks as it harms the users. Due to the self-balancing nature of DEXs, the price of the bought asset increases after the swap—the more considerable the exchanged amount, the greater the price increases. Sandwich traders take advantage of this by purchasing an asset for cheap before a large trade passes through and selling the asset afterward for a higher price. This increases the slippage of the targeted user leading to a loss.
The Good and Bad of MEV
MEV is an important part of our ecosystem and brings various advantages. DeFi, for example, has stable prices across DEXs due to arbitrage traders, and lending protocols can ensure fast liquidations to protect their lenders. But MEV also has its downsides.
MEV extraction can also damage the user through higher slippage due to sandwich attacks or higher network fees caused by gas wars amongst bots that fight to be included in the next block.
Because more searchers are coming in with the growing popularity of DeFi, another growing concern is that MEV rewards might soon outweigh block rewards. This might tempt selfish miners to re-mine blocks to capture the MEV themself, causing instability in the consensus mechanism and therefore rendering a threat to Ethereum. A solution for this issue might be MEV Smoothing.
MEV is also very specialized. The better you are at it, the more profit you make, and thus more resources you can put into running different strategies on various protocols. This can have a centralizing force on block builders and could prove to be an existential threat to the entire ecosystem. Many blockchain researchers are investigating solutions for this problem, primarily PBS (proposer builder separation).
State of MEV
Maximal Extractable Value (MEV) gained popularity in early 2021 and became an essential part of the ecosystem of Ethereum and many other chains. While many searchers are making good financial gains, the growing competition makes well-known MEV opportunities harder and less profitable to capture. This benefits miners/validators as they receive profit shares and more gas fees through gas bidding amongst bots. To remain profitable as a searcher, it is recommended to practice MEV on other chains or look for less-well known tactics.
DEX Projects
1inch Network Does More
Author: Ap0ll0517

The 1inch Network is so much more than an Automated Market Maker (AMM). It’s a decentralized exchange (DEX) aggregator. Unlike other AMMs, which rely only on their own liquidity pools to facilitate trades and swaps, 1inch allows access to liquidity across multiple DEXs. That means trades executed on 1inch could use liquidity pools on Uniswap and other AMMs like Sushiswap, Balancer, or Quickswap.
Since its initial launch in 2019, it has developed additional DeFi tools such as the Aggregation Protocol, Liquidity Protocol, Limit Order Protocol, P2P transactions, and 1inch Mobile Wallet. All of these tools give investors more flexibility and options when it comes to trading. They ensure that users’ capital is utilized in the most efficient manner.
Aggregation Protocol
The 1inch Aggregation Protocol is a routing algorithm. It searches different AMMs for the best exchange rate between assets. It can also split a token swap between those other protocols, or utilize different liquidity pools within the same one. This means that an exchange could come from multiple sources of liquidity. For example, an exchange could be split up with 50% from Uniswap V3, 34% from Uniswap V2, and the remaining amount from Balancer.
This is unique because it ensures users receive the best exchange rates. Whenever there is an exchange of assets from a liquidity pool, the exchange rate continually updates. This is happening simultaneously as the exchange is processing. That means the first half of your trade could be exchanged at an attractive rate, but the second half is traded at a much less attractive rate.
The routing algorithm can calculate and compare all the different exchange rates across all the different sources of liquidity. It will only use a liquidity source until that exchange rate is no longer the best rate. The rest of the trade will then be routed to the next liquidity source with the best exchange rate.
There is access to over 50 liquidity sources on Ethereum, more than 20 on Binance Smart Chain, and at least seven on Polygon. The Aggregation Protocol also has access to liquidity on Optimism, Arbitrum, Gnosis, Avalanche, Fantom, and even Klayton network.
Liquidity Protocol
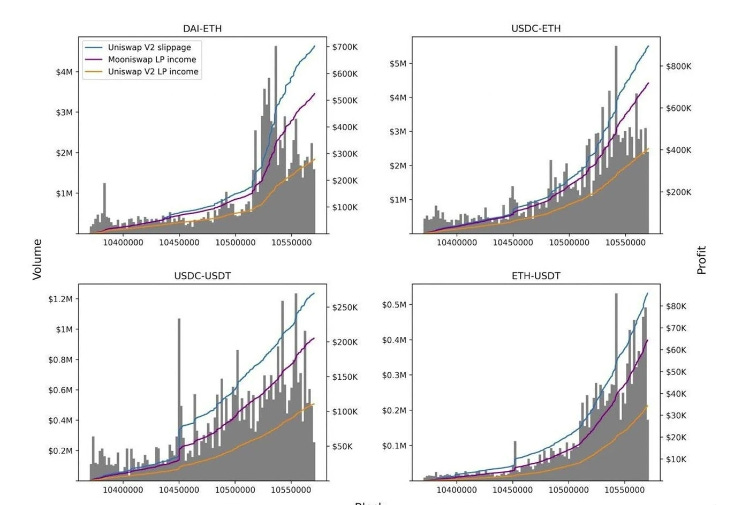
The 1Inch Liquidity Protocol has its own AMM, Mooniswap. Similar to Uniswap, Mooniswap uses liquidity pools to execute trades and replace the traditional order book. However, unlike Uniswap, Mooniswap uses a time delay function to reduce slippage and arbitrage opportunities. When a trade is executed, this AMM does not automatically update or display the new exchange rates for upcoming trades. The exchange rates for arbitrage opportunities update slowly, over approximately 5 minutes. As a result, arbitrageurs can collect only a portion of slippage, with liquidity providers sharing the rest. According to the 1Inch team, Mooniswap liquidity providers (LPs) are expected to earn 50% to 200% more profit than Uniswap V2 LPs.
Limit Order Protocol
The 1Inch Limit Order Protocol allows users to place limit orders with their crypto assets. A limit order is a request to buy or sell an asset at a predetermined price. This offers users extreme flexibility since they can create an order and simply wait for it to get filled without trying to perfectly time the market. 1Inch also allows users high gas efficiency as the orders are placed off-chain and later filled on-chain. Placing orders off-chain permits users to take advantage of the gasless limit order feature. Whoever places the limit order doesn’t have to pay any gas fees as they are simply signing a message, which is an off-chain transaction. However, the person filling the order is responsible for paying gas fees because they will be executing an on-chain transaction.
P2P Transactions
1Inch P2P Transactions allow users to make trades and swaps privately with each other. Instead of using the Mooniswap, or the routing algorithm to find the best exchange rate from other sources of liquidity, a user can decide to execute an exchange with a specific address. This gives users more control of who they trade with. Typically, whenever a user wants to sell or purchase assets from other AMMs, they have no idea who the counterparty is. They are only engaging with the liquidity pool. As stated earlier, whenever there is an exchange of assets from a liquidity pool, the exchange rate changes. Whales interacting with liquidity pools can drastically modify the exchange rate. However, if two whales were to trade with each other instead, the exchange rate of the liquidity pool remains unaffected.
Users can also determine the exchange rate - just like a limit order. This uses the same gasless feature we see with the Limit Order Protocol. After the exchange rate is set and the counterparty is determined, users can also decide on an expiry time for the order. It could expire in 10 minutes, an hour, a day, or even last indefinitely. Once all these details have been confirmed, a custom link will be generated to share with the counterparty. Only the defined counterparty wallet address can open the link and continue executing the trade.
1inch Mobile Wallet
The 1inch Mobile Wallet is noncustodial. This means that users are responsible for maintaining the safety and integrity of their private keys. 1Inch Mobile Wallet is designed to give users the best crypto experience while safeguarding their assets. Not only is it available for both Android and iOS users, but it also comes fully equipped with a wide range of features. Possibly the most convenient feature is the fiat on-ramp. Users can purchase many different cryptocurrencies without having to use a centralized exchange. As soon as their purchase is confirmed, assets are sent to their wallet without the need for additional transfers.
Of course, the routing algorithm is included in the wallet so users get the very best exchange rates when swapping tokens and coins. The 1Inch Wallet also allows users to connect to dApps with its built-in Web3 browser and comes with multichain integration. Eight blockchain networks are supported with chains such as Gnosis, Avalanche, and Klaytn already added to the interface so users don’t have to worry about adding them individually.
How 1Inch Handles Governance
1INCH is the governance token of the 1Inch Network DAO. Launched in December 2020, 1INCH has a current supply of 1.5B tokens with just over 38% in circulation right now. This token is used to vote on governance proposals. Anyone is open to participating in governance discussions, but only 1INCH holders may vote. First, they must deposit their 1INCH into a staking contract. This ensures that all governance participants have a vested interest in the protocol’s success.
After staking their 1INCH tokens users will receive st1INCH, which is a nontransferrable token used to vote. The amount of st1INCH received is relative to the number of 1INCH tokens staked in the contract. Not only does staking 1INCH tokens allow users to engage in governance, but it also rewards users with a special incentive called the gas refund program.
Under this program, additional 1INCH tokens are distributed as a gas refund to Ethereum users who stake 1INCH through the 1inch dApp. Depending on the amount of 1INCH staked, users can receive up to 100% of gas fees refunded to them.
Matcha
Author: Kris
One of the most important developments in the decentralized finance world is the steady rise of DEXs and Automated Market Makers. And with so many of these protocols coming on line, the need for aggregators like Matcha has become essential. Just like searching for better airfares using search engines or aggregators like Google Flights, Expedia, or Priceline, Matcha searches far and wide to make sure you’re getting the best prices on your DeFi trades.
Matcha is a consumer-facing DEX built by 0x Labs, an OG company behind the 0x Protocol, which builds tools to help people deploy decentralized exchanges. In essence, Matcha uses 0x technology to act as a decentralized exchange aggregator. Matcha currently has the second most volume of any DEX aggregator, behind leader 1inch.
Matcha utilizes the 0x API and 0x Mesh to leverage aggregated liquidity and price information from over 50 of the top DEXs, including Uniswap, Kyber, Curve, Bancor, and Mooniswap – so you know you’re getting the best prices - all in a single, easy-to-use interface. On top of that, it also optimizes for gas, which helps makes it cheaper than going directly to Uniswap, SushiSwap, or PancakeSwap. Knowing that you’re shopping all DEXs at once, Matcha makes trading simpler, more enjoyable, and more profitable than ever.
Convex
Author: Hiro Kennelly
In the last edition of the DeFi Download, we covered Curve. Curve is a DEX and AMM with deep liquidity that is known for having low trading fees and minimal slippage, and for using a time-lock governance mechanism that also affects the tokenomics of CRV, Curve’s governance token. Curve is a cutting-edge protocol with innovative incentive structures, so it’s no surprise that in the world of composable DeFi money legos, other protocols have attempted to capture some of these incentives for token holders. The most successful of these protocols is called Convex.
Curve Tokenomics
Those of us who have been in the DeFi space for the last couple of years have probably heard of the Curve Wars. To understand the Curve Wars and the rise of Convex, it’s important to have a basic understanding of Curve tokenomics. As with many protocols that incentivize liquidity pools, Curve liquidity providers receive a percentage of the trading fees and native-governance tokens as rewards. Curve brings the incentivization model one step further by allowing CRV token holders to lock their CRV tokens for up to four years. In return, these depositors receive vote-escrowed CRV (veCRV) tokens, which allow holders to participate in Curve governance, including directing CRV reward emissions to liquidity pools. The veCRV holders also receive additional trading fees and their LP positions get ‘boosted’, receiving higher yields. All of this combined creates a hot market for CRV, especially during bull runs.
The Curve Wars
Many projects with native-governance tokens saw Curve’s tokenomics as a way to boost the liquidity of their own tokens. To maximize returns for these liquidity providers, protocols battled to secure the most veCRV. This battle to secure veCRV is known as the Curve Wars, and the winners of this war would get to direct CRV emissions, receive boosted yield on their liquidity pool, and earn trading fees. This is where Convex comes in.
The Rise of Convex
Convex is essentially a Curve usability layer that rose to prominence during the Curve Wars because it made it easy for users to receive the fully boosted yield on Curve’s incentivized liquidity pools, all without being subject to veCRV’s locking period.
There are a five main ways users can participate in Convex:
1. Curve LP Tokens

Users can deposit Curve LP tokens into Convex liquidity pools to earn boosted yields and CRV reward tokens without needing veCRV, that is, without needing to time-lock CRV, nor the large LP positions to maximize rewards. The flexibility and incentives that Convex offers Curve LP token holders is a huge draw to the platform.
2. CRV Tokens

Users can deposit CRV into Convex, which is then locked on the platform forever as veCRV. In return for providing this CRV (that becomes veCRV) depositors receive cvxCRV, a synthetic veCRV, on a 1:1 basis. The cvxCRV token provides a type of liquidity veCRV does not, as cvxCRV can be swapped for CRV, and their prices, while not perfectly pegged, track well.


3. Stake cvxCRV Tokens
The main reason to have cvxCRV is to stake it. Users can stake cvxCRV to earn additional CRV rewards, trading fees, and CVX tokens. CVX is Convex’s native-governance token. cvxCRV is essentially liquid veCRV, and staking it provides similar rewards to receiving the veCRV boost in Curve, plus CVX. This formula has proved so popular that Convex currently controls nearly 50% of all veCRV tokens, as indicated by the supply of cvxCRV tokens relative to the circulating supply of veCRV tokens, as seen below.

4. Stake CVX Tokens

Users can stake CVX tokens, which entitles them to trading fees in the form of cvxCRV tokens.
5. Lock CVX Tokens

CVX holders can also lock their CVX tokens to receive additional platform fees and governance rights, including voting weight and the ability to direct CRV emissions. The minimum vote-lock time is 16 weeks plus seven days. These vote-locked CVX tokens accrue rewards, as they are automatically staked, and there is a slight boost in yield.
Because Convex controls so many CRV tokens, it’s said that Convex is now the real battleground of the Curve Wars, and for protocols that are looking to supercharge their liquidity pools it now makes sense to HODL CVX tokens rather than CRV tokens.
Vote Bribery
One interesting collateral episode is that the protocols involved in the Curve Wars are now essentially paying bribes to CVX token holders to encourage them to vote to reward their liquidity providers. There are multiple protocols facilitating this vote-buying, most notably Votium. These bribes add another financial incentive to CVX.
A Parabolic Rise
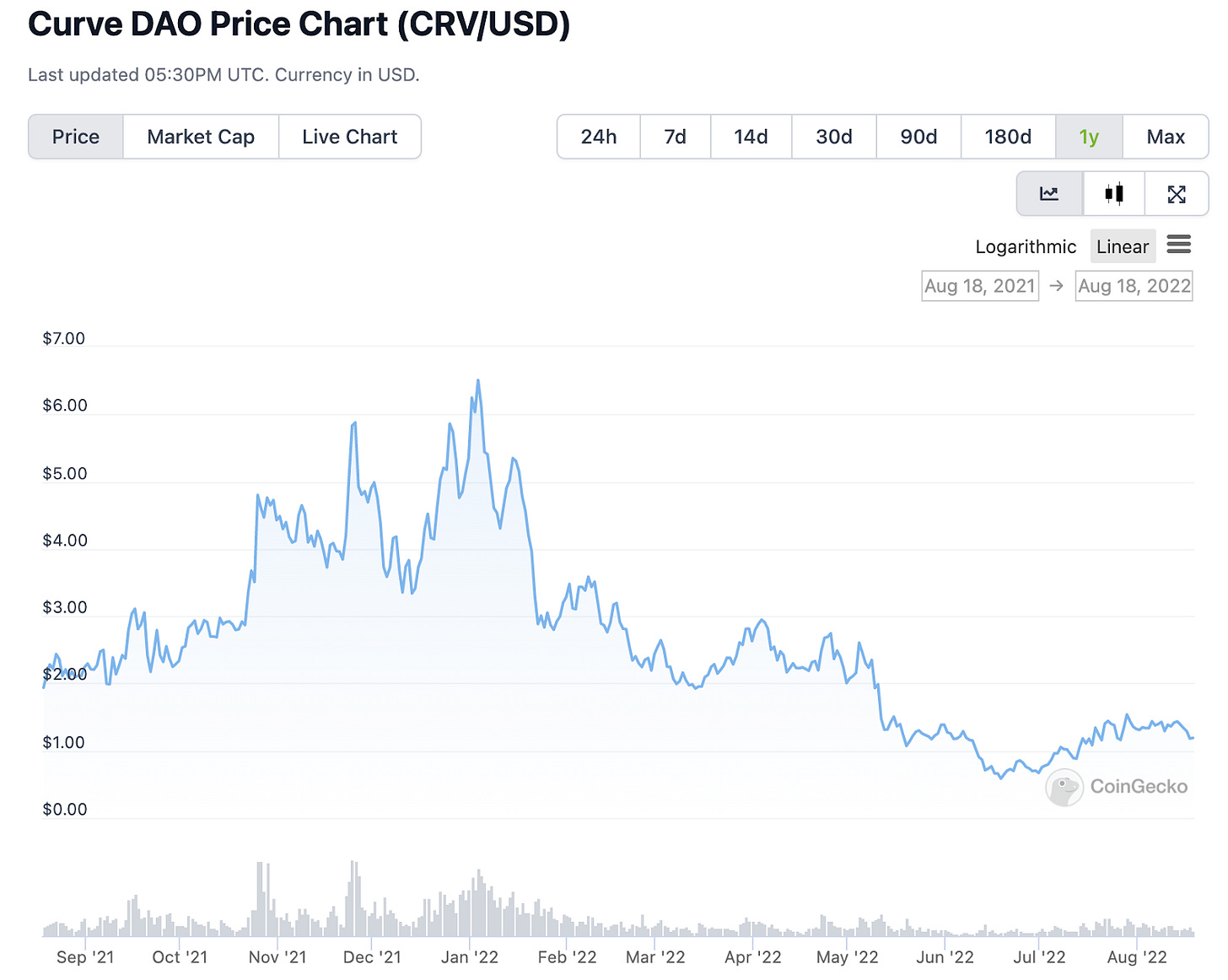
A convex is a type of parabolic curve, and given Convex’s quick ascent it’s perhaps a fitting name for a protocol built to simplify and amplify Curve’s tokenomics. Convex’s complex tokenomics scheme involving Curve LP tokens, CRV, cvxCRV, and CVX plus bribes provides a supercharged incentive model, so it’s no wonder that Convex has grown to have a TVL of 4.5 billion USD, sitting in sixth place just behind Curve’s 6 billion USD TVL, according to DefiLlama.
While it’s clear that when CRV is more valuable, CVX is too, it’s worth noting the CVX is currently trading at nearly 4 times CRV’s value — and, when CRV had a higher value, that multiple increased. While #DYOR #notinvestmentadvice, you’d do well to look at the chart below and consider Convex if you’re bullish on Curve.
Rook
Author: Jake and Stake
Over $585 million dollars in MEV has been captured from blockchain networks (according to flashbot.net) and Rook’s mission is to give this value back to users, protocols, and market makers. They offer a trading platform where users get to trade for free.
In fact, Rook pays users with the MEV that their trades emit. The canonical example of MEV is price arbitrage. When users submit transactions to a DEX, bots called “Keepers” analyze the transaction and figure out how to extract value from it. Whenever there’s a price discrepancy (and there usually is) bots will take your trade and back-run, front-run, or both (perform sandwich attacks).
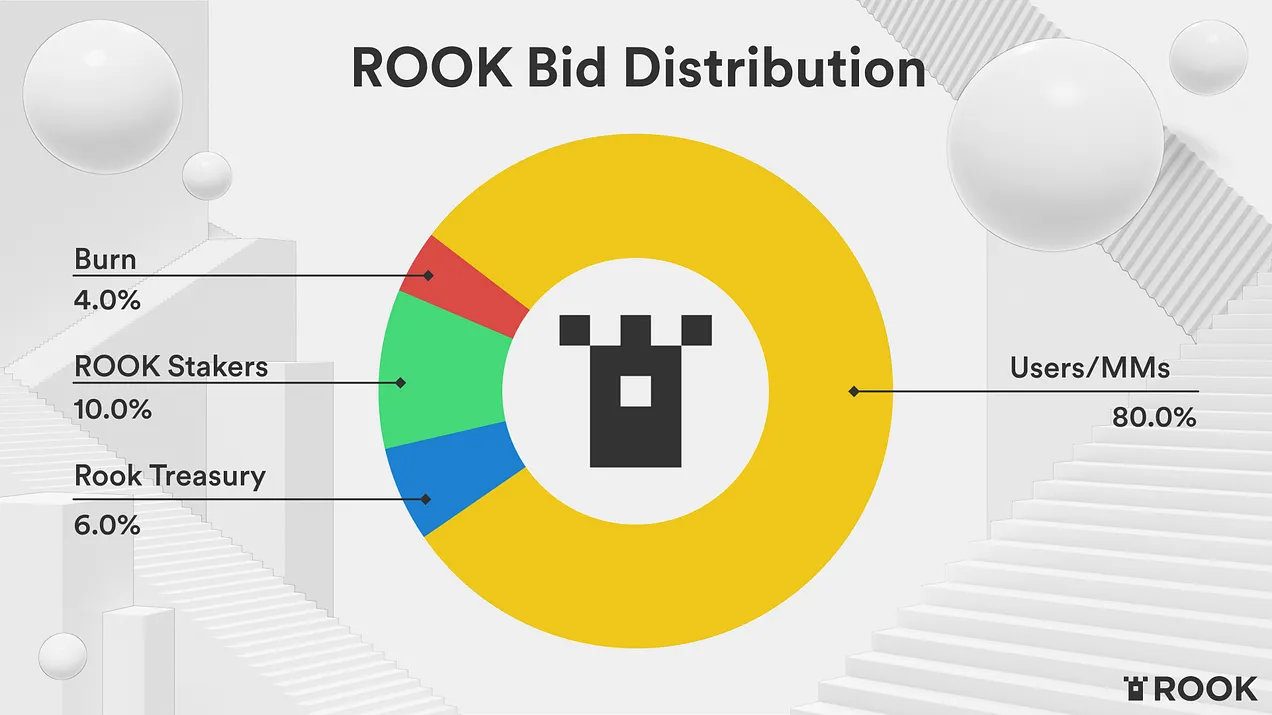
Rook is a protocol that captures this value and distributes it back to users. Rook can access a variety of liquidity sources which gives users better prices, reduces slippage, and increases profits. By trading with Rook, users get access to a variety of liquidity pools and they get 80% of the MEV upside. Users also get to trade for free because gas fees are subsidized by MEV.
How does Rook Work?
Rook builds on top of existing AMM protocols like Uniswap and Sushiswap and DEX aggregators like 1inch and Matcha.
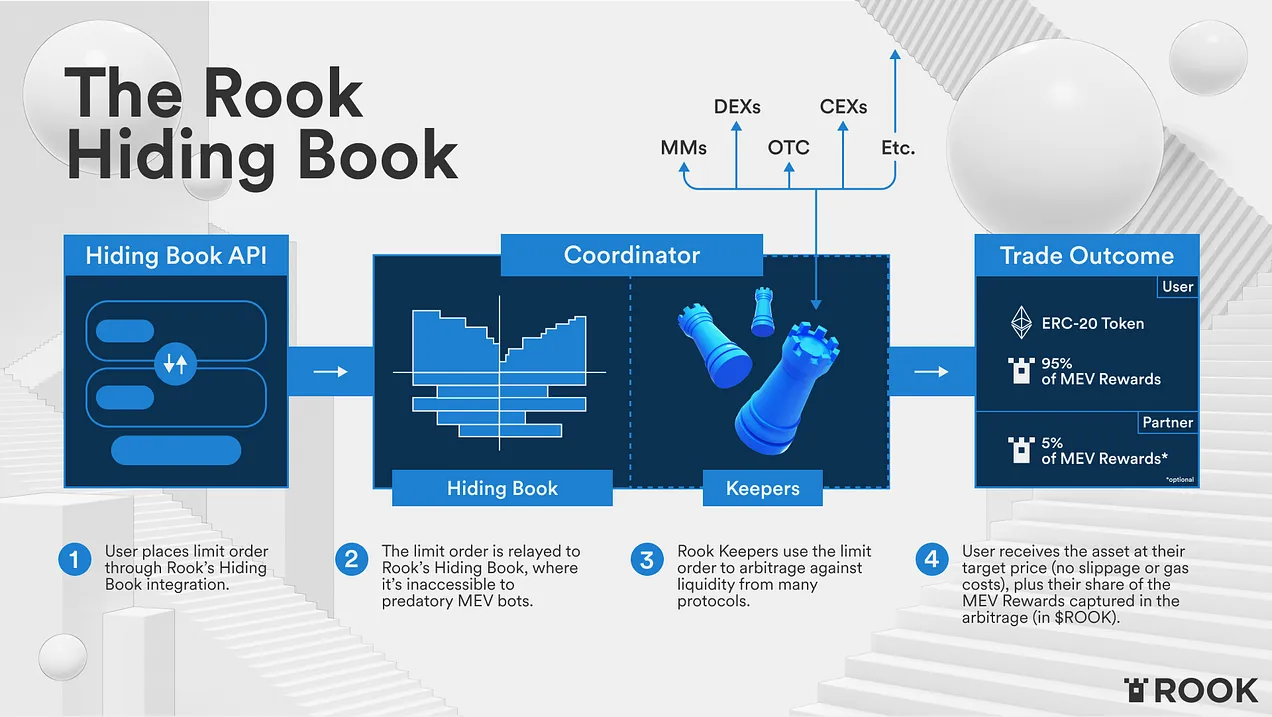
Users submit transactions to Rook’s web application which is then sent to the off-chain order book called the “Hiding Book”. Participating keepers take those transactions and look for profit opportunities across DEX protocols, CEXs, and other orders in the book to execute the trade.
These keepers search for MEV opportunities, capture that arbitrage, and distribute it to the trade’s originator whether they be users or market makers.
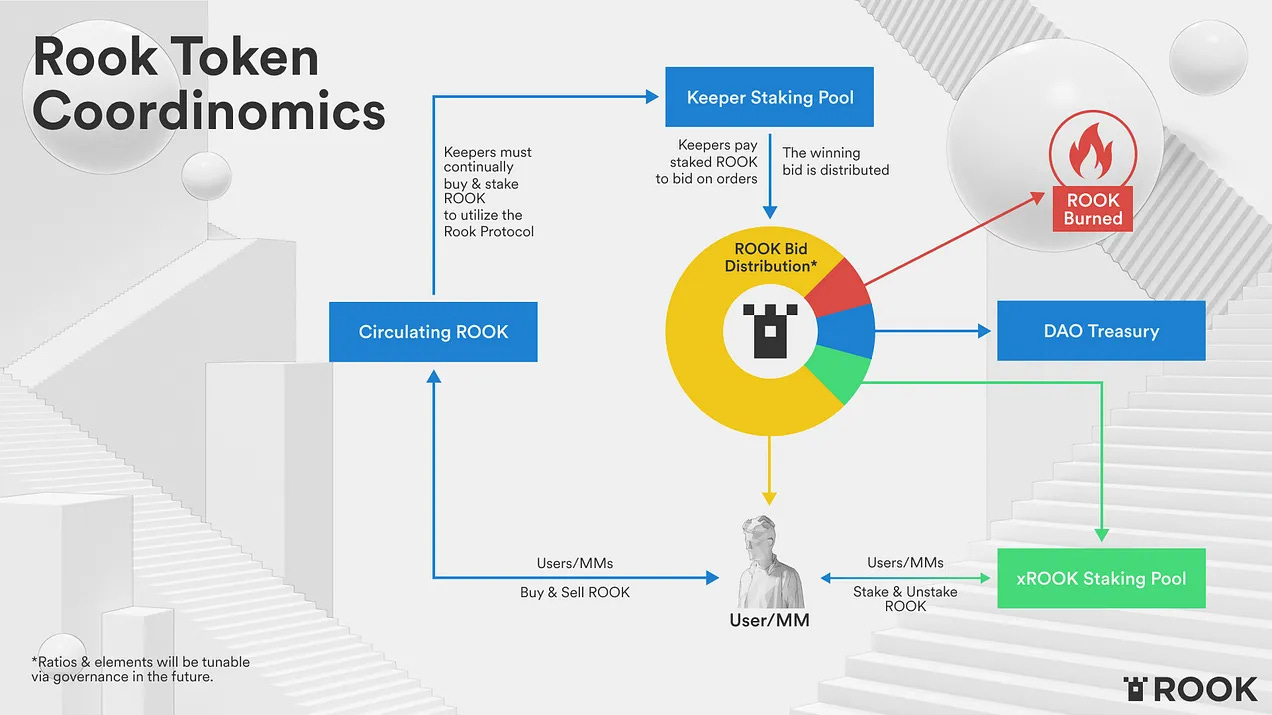
The entire protocol is centered around the Rook token. Users can stake it to earn rewards, but keepers must also purchase it in order to participate in the protocol. They use a separate staking mechanism to place bids on orders in the Hiding Book. Eventually, the bid is split across a variety of entities; namely, trade originators, the DAO treasury, and the user who have Rook staked in the protocol.
Here’s a step by step walk-through of the lifecycle:
Keepers buy ROOK and stake it in the Coordinator smart contract in order to bid for the right to execute transactions.
Keepers watch incoming transactions, and use their access to all on-chain and off-chain liquidity to find the most optimal and profitable way to profitably execute them.
When an opportunity is discovered, an auction is held that will decide the Keeper that gets to execute the transaction. In the auction, Keepers place bids using their staked ROOK from (1).
The protocol algorithmically balances upward and downward bid pressure to discover the fair value of the profit opportunity.
The winner of the auction broadcasts and executes the user’s transaction collecting the profit they discovered.
The profit is shared with the trade’s executor, the DAO’s treasury, and users that have ROOK staked, while some is burned.
This has the effect of making ROOK deflationary. Because Rook keepers must use it to participate in the protocol, there’s upward price pressure. The burn mechanism also increases that price pressure by decreasing supply.
So What?
What’s novel about Rook is that they’ve integrated MEV into their AMM. Because keepers are constantly looking for arbitrage opportunities, they search across a variety of liquidity pools. The benefit is that users and market makers don’t have to integrate their systems with all these pools themselves. Rook handles it for them.
The tokenomic incentive design is quite clever. All this value is funneled directly into the ROOK token, benefiting holders and users alike. Given sufficient volume, users paid for trades, keepers get easy MEV opportunities, and Rook holders get a deflationary asset.
Actions steps
📖 Read What explains the rise of AMMs? | Hassebq
⛏️ Dig into On Path Independence | Vitalik
🎧 Listen How do Liquidity Pools work? | Finematics
🙏 Sponsor: Oasis.app - Borrow Dai & Earn
Project Releases 🎉
Hand-picked articles to understand the current state of the DeFi ecosystem
The Liquidity Pool (MLP) for Mycelium Perpetual Swaps
MLP(Mycelium liquidity pool) is a basket of blue-chip assets and stable coins pooled together, which acts as a global AMM for leveraged trading.
LPs can deposit any whitelisted asset into the MLP pool in return for MLP tokens, which represent the LPs' share in the diversified pool
$5Mn MLP deposited in the first 48 hours!

Token Bridging on Rubicon
Bridging route on popular token bridges, with support for nine major blockchains and dozens of token combos
More than $1 billion of user funds were lost in bridge hacks in the past year. With this bridge integration, Rubicon traders can seamlessly transfer crypto assets across chains without having to leave the app

DFS Automation for Aave v3 on Arbitrum
Automation is a unique service providing different automated options for the DeFi positions in a trustless and non-custodial manner.
Automated strategies allow liquidation protection in the form of deleveraging (partial unwinding) in case of markets moving down and automated leverage increase in case of markets moving up.


GameStop wallet integrated with Immutable X L2 protocol
GameStop wallet integrated with the Immutable X Link infrastructure, making the wallet natively compatible across the entire protocol.
This integration allows any Immutable X marketplace or partner that supports Link to natively offer the GameStop wallet as an option to connect and trade.

Coinbase Prime now offers Ethereum staking to institutions in the US
With Coinbase Prime, institutional customers can stake their ETH and several other assets to begin generating yield.
Institutions can create a wallet, decide how much to stake, and initiate staking on their Coinbase Prime account.

Risk Harbor Core V2 Now Live on Arbitrum
Risk Harbor Core V2 solves the problem of insufficient underwriting capital using vaults. Alongside vaults, Risk Habor developed an Automated Market Maker (AMM) tailored to risk management marketplaces.
The AMM understands risk programmatically and prices protection accordingly. The AMM also allows the vault to enter leveraged positions, which is the fundamental pillar of generating competitive rewards for users providing capital.
Users can purchase protection on any of the pools in Core Vault 5.


Chirping Birds 🐤
🔥 and 🧊 tweets from across the DeFi ecosystem





Tokenomics 101: veTokens vs Valueless Governance Tokens
Author: Jake and Stake
Many DeFi tokens were created to incentivize liquidity for their products and allow their community to help govern the project. This “Valueless Governance Token” model has the following properties:
Avoidance of regulatory scrutiny
Governance powers
Zero claims on the project’s cash flows
Little utility outside of trading
Often, the supply of these tokens will inflate as they’re used to incentivize behavior—often to attract liquidity. These aggressive token emissions lead to high supply and low demand, but to counter this dynamic, several protocols have implemented a new tokenomic model: Vote Escrow Tokens or veTokens. The many protocols that have implemented this include Cream, Curve, Pickle, and Convex.
What is a veToken?
The “ve” in veTokens stands for vote-escrow. Token holders can deposit their governance tokens into the protocol for set periods of time (escrow) in order to get a share of fee revenue or special privileges (like voting). This was pioneered by Curve Finance with the veCRV token.
With Curve, users lock CRV tokens into the protocol in exchange for non-transferrable veCRV tokens. Users have the ability to lock their tokens for one week to four years, with increased incentives for longer time frames. veCRV holders get special privileges like:
Governance rights: Particularly the ability to direct the protocol’s token emissions to particular pools. This means veCRV holders have control over each pool’s yield and thus liquidity, making CRV tokens extremely valuable and increasing demand.
Claims on trading fee revenue: 50% of all trading fees are distributed to veCRV holders. Users get a share of trading fees via the 3CRV LP tokens—the Liquidity Provider (LP) token for Curve’s 3Pool. This stablecoin pool has the deepest liquidity in DeFi and is composed of DAI, USDT, and USDC.
Boosted CRV emissions: LPs that have CRV locked earn additional rewards of up to 2.5x CRV.
In essence, token holders forgo their liquidity for increased perks and powers within the protocol, coupling voting power and token emissions.
Long-Term Involvement Through Lockups
The lockup periods of CRV encourage a long-term mindset. If you can’t sell a token for 1-4 years, you’re going to think about how to create the maximum amount of value for that protocol when that time frame is over. This could mean adjusting protocol incentives to forgo short-term profit seeking.
Compare this to the typical mercenary capital used to LP, where tokens are dumped as quickly as they are purchased. We’ll talk about Convex (CVX) later in the article, but some of the largest veTokens have lock up rates of over 50% on average.

The generous CRV emissions increase supply, but are offset by the demand for them to be locked up.
Incentive Alignment
Because the CRV token emissions are distributed to the protocol participants that primarily demand the token for its perks, there’s reduced sell pressure. In Curve’s case, this creates a reflexive environment:
veCRV directs CRV rewards to some liquidity pool. This can be any pool, but let’s call it “Pool X”.
LPs for Pool X get more CRV and then lock up CRV for veCRV.
LPs use veCRV to direct more CRV rewards to Pool X.
Without the veToken model, LPs would have no incentive to reinvest and simply sell their CRV rewards. However, with veTokens, LPs eventually become the majority token holders. There used to be a zero-sum dynamic where token holders and LPs fought for fee share, but now the largest token holders will be the people that provide the most value to the protocol: LPs; and because all token holders are incentivized to lock their tokens, sell pressure is weak.
Downsides of the veToken Model
Centralization of Token Ownership
Token emissions change who has control of the protocol, and because of the returns to scale, more tokens will be distributed to fewer players. If a few large players have control of the protocol, they may try to extract as much value out of it as they can. They can also tank the protocol via token sales.
Opportunity Cost
Another consequence of long lock up periods is the token holder’s inability to react to volatile price movements. Users that lock their tokens cannot move their money elsewhere. Their liquidity is locked in, making them completely exposed to price falls. This has led to projects like Convex, that create liquidity for users via their derivative cvxCRV.
Vote Selling and Bribes
Vote selling and bribes have the potential to create cheap ways to influence the protocol. This commonly takes the form of token holders being offered money to vote a certain way.
The sale of votes can lead to those non-long-term actors to make protocol-wide changes. These proposals can be short-sighted at best and extremely risky at worst, leading to unintended consequences.
I’m not sure these downsides can be neutralized without some creative token engineering, but the value of this new tokenomic model is a testament to the innovation happening in web3. Projects are already building on top of this foundation, namely Convex.
Convex
Convex has entered the chat, with the intent to corner the Curve market. Their strategy is to capture as many CRV tokens as possible in order to have majority control over token emissions. They’ve done this by:
Creating a liquid veCRV derivative.
Providing a platform for liquidity providers and CRV token holders to combine their assets and boost their rewards.
Protocols have taken notice. The ability to direct CRV emissions to particular liquidity pools has become extremely valuable to protocols because it directly incentivizes liquidity. Projects are now paying Convex “bribes” to direct CRV emissions to their token’s pool. This not only incentivizes liquidity growth, but if the project already has a large LP position, they can earn CRV tokens as well.
Incentives for…
… CRV Stakers
The protocol rewards users that stake their CRV on Convex with a share of the boosted CRV on the Convex platform. Users earn shares of the Convex “platform fees” (details below), trading fees from the Curve Platform (3CRV), and CVX tokens.
Convex users also remain liquid via the cvxCRV token. When users deposit their CRV into Convex, those tokens are locked forever. Convex is continually accumulating CRV tokens, thereby increasing its voting and governance power. However, users get liquidity for their tokens because Convex issues a derivative that represents the veCRV tokens: cvxCRV. This token is issued at a 1:1 rate.
Somewhat surprisingly, the prices are relatively similar:
This points to an efficient market for CRV and cvxCRV.
… Curve LP Stakers
Users can use Convex to stake their LP tokens and earn rewards. Users that stake their LP tokens with Convex get the following advantages:
Typical rewards from veCRV (3CRV + any airdrops)
A share of 10% of Convex LPs’ boosted CRV earnings
CVX tokens
Liquidity providers utilize Convex to boost their CRV rewards without locking CRV themselves. Because LPs get boosted rewards if they have CRV locked in the protocol and because Convex already has a lot of CRV locked up, LPs can work with Convex to get the maximum rewards. This modularizes the LP + CRV requirement.
Note that there are fees for staking Curve LP tokens based on the profit of your LP position:
10% is distributed to cvxCRV stakers
5% platform fees are distributed to CVX stakers (as cvxCRV)
1% operation fees are sent to harvesters (for gas fees)
… cvxCRV stakers
Like CRV, users can stake their cvxCRV on the Convex platform. Convex has a 16% fee where they earn CVX tokens, platform fees in the form of CRV, and veCRV rewards (3CRV).
… CVX stakers
The CVX token can also be staked to earn more cvxCRV tokens. As mentioned above, 5% platform fees—protocol revenue—are distributed to CVX stakers (as cvxCRV).
Final Thoughts on veTokens
Due to the reflexive design, incentivized token lock-ups often make “number-go-up”. An additional benefit is that protocols get more flexibility with respect to paying contributors.
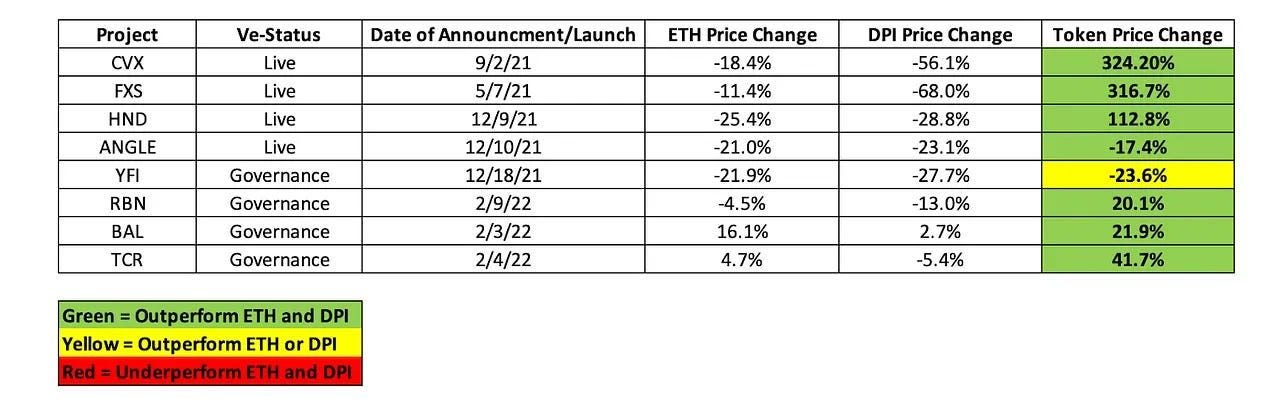
The veToken model is a relatively simple idea: lock up tokens and give people new powers, such as governance rights and access to increased returns. It also allows protocols to incentivize long-term behavior and gives these players a larger proportion of tokens. If implemented well, it reduces the sell pressure and offsets token emissions.
There are some risks of course. Centralization and short-term decision making being the most perilous to navigate. That said, this tokenomic model is an ingenious way to redesign incentives. This is the essence of crypto: we design the incentives and rules of engagement without the need for an intermediary. It’s up to us to figure out new ways to slay Moloch.
The next innovations for this model will be figuring out new perks for stakers and how these powers will holistically affect the protocol, given that tokenomics designers can use veTokens to redistribute power to particular groups. In Curve’s case, it was the LPs that grew their power, but this design can be used across a variety of projects.
⚠️ Security Scares (Part I): The Slope/Solana Pillage and Implications of Supply Chain Attacks on DeFi
Author: d0wnlore
There is no shortage of heist stories and security incidents to report on in crypto. Just one day before the events of the Solana incident involving the Slope mobile wallet, which will be the focus here, the multi-chain bridge Nomad had suffered one of the largest attacks in recent months. In this situation it’s difficult to choose what to cover in a biweekly editorial while serving both incidents their due respect.
But here we will cover the Solana incident, where thousands of addresses that interacted with the mobile wallet Slope had their tokens forcibly removed. While deploying vulnerable smart contracts is nothing new in DeFi, supply chain attacks are quickly becoming a growing concern, as it has been in the Web2 world for several years. Because many DeFi protocols still rely on Web2 companies to deliver a polished product, we need to be cognizant of the weaknesses in this relationship and what our community can do to mitigate further damage to both our wallets and the optics of crypto being secure.
The Incident
On August 2, thousands of Solana wallets were drained and emptied into other wallets used by the exploiter. As news broke out, so too did the crypto community, culminating in a mass of questions, rumors, and speculation. But as the dust settled, we started to realize that this wasn’t your typical mass token removal incident, where many victims will have interacted with the same malicious smart contract.
In this incident, the transactions were signed and transferred from wallets directly, suggesting that the mnemonic phrases and/or private keys of those wallets were leaked. As investigations from several security researchers and companies continued, we got a clearer picture of what had occurred (and more details may be brought to light after the time of this writing):
Compromised wallets interacted with with the mobile wallet Slope, either through the generation or importing of their mnemonic phrases through the wallet (this does not affect hardware wallets that interacted with Slope).
It’s likely that these mnemonic phrases were leaked to third party vendors that provide telemetry and analytics data to Slope. Thus far it has been suggested that at least Sentry, an error reporting service used by the Slope wallet, may have been given mnemonic phrases in clear text.
The leak of secrets to third party vendors seems to be the most likely scenario. This is what we would call side-channel leakage, where data is leaked to unattended parties (vendors) or other channels (log files) when that data is being handled. In this case, Sentry is sent mnemonic phrases in clear text that should not have been made available to the script that parses data to be sent to the error reporting service.
But this doesn’t completely solve the mystery. While Sentry would now have the critical data of thousands of wallets, that data is still contained within Sentry’s servers. While this data could have also been leaked in-transit from the mobile wallet to Sentry, it’s unlikely due to HTTPS being used in the requests sent to Sentry, which would encrypt the relevant data being sent.
This is where speculation of the current situation remains, as it suggests that either someone has abused—and is still abusing—privileged access to this data in Sentry, or there are other vendors where these secrets are being leaked to and could also have had privileged but unauthorized access to that data. If this is the case, then we also have another type of attack on our hands, called a supply chain attack, where those with privileged access to a third-party system or data abuse that privilege to attack that system or steal that data.
History Rhymes
Supply chain attacks are not new and we have seen these attacks on several DeFi protocols in the past. Here are just a few highlights:
BadgerDAO front-end compromised through CloudFlare Workers: https://badger.com/technical-post-mortem
A malicious contractor injecting their own wallet address into SushiSwap's MISO launchpad: https://arstechnica.com/information-technology/2021/09/cryptocurrency-launchpad-hit-by-3-million-supply-chain-attack/
The DNS hijacking of many DeFi protocols through the same domain registrar, GoDaddy: https://quickswap-layer2.medium.com/quickswaps-godaddy-domain-hijack-how-it-happened-our-proposal-to-restore-the-community-35be9ddbb19a
There are many other attacks on the periphery of supply chain attacks that we still have not seen on a large scale in DeFi or Web3 yet, such as subdomain takeovers. But it is only a matter of time before those become a concern for us as well. Many of these occur due to lack of knowledge of all pieces that contribute to your project: technical assets, software dependencies, and the entities that own those assets and dependencies.
Takeaways
Web3 supply chain attacks often have a direct impact on users as they are usually done in order to steal private keys or manipulate users into performing bad transactions. Whereas in Web2, many supply chain attacks are used to undermine the target company and steal and/or wipe out their data, with varying impact on the end user. These takeaways apply to users and protocol developers. But what is unique about crypto is the willingness for both of these parties to work together to solve problems faced by both.
The number of software dependencies used by protocols must be reduced and should be open-sourced if they have any privileged access to your protocol or app. If that’s not possible users should have some way of being able to verify the code does as expected and nothing else.
This incident is another hard lesson learned on the benefits of using a hardware wallet, where there’s only one vehicle for your private key and that vehicle never actually lets anyone else see it (be sure to store your recovery phrase securely, as well).
Users may need to exercise more due diligence when interacting with protocols. Use the standard tips for detecting phishing websites, and apply the necessary precautions when interacting with contracts. The contract you’re interacting with may be a phony.
Start adopting more security practices that Web2 companies perform such as red teaming and threat hunting.
The more of these web2-like incidents that we encounter in crypto, the less attractive the ecosystem starts to look for those with a low risk-tolerance. They will start to question the security of blockchain ecosystems and question benefits of using these DeFi protocols over their TradFi or FinTech banks.
Supply chain attacks have lead to some of the worst cyber attacks in recent history that have harmed both organization reputations and individual people and groups. But if we don't stop them, or at least slow down their pace, then we will also face issues with growing the DeFi and Web3 ecosystem.
⚠️ Security Scares (part II): Curve Compromised
By: Austin Foss
Even if your project does everything right – everything that could have been done to protect your users has been done – something can, and often does, still manage to go wrong. On Tuesday August 9, 8:40 PM UTC, Curve Finance (CRV) announced on Twitter that something had indeed gone quite wrong.
In the Blink of an Eye
The incident was first reported by samczsun on Twitter, corroborated by @LefterisJP, until finally confirmed by CRV; the total time from initial tip-off to an official warning was just 15 minutes. Shortly thereafter, CRV disclosed more information about the attack:
The name server (NS) was likely the point of failure.
Something on the registrar’s site, iwantmyname, had gone wrong, but it was not likely related to CRV's account.
While curve.fi was affected, curve.exchange was considered likely to be safe since it "uses a different DNS provider", but users were still warned to proceed with extreme caution.
It only took one hour after that initial tip-off before CRV fixed the problem by reassigning their domain to a different authoritative NS and having it point back to the proper IP address of the real front-end host. This still took a total of 25 hours to take full effect while the DNS update was propagated to all NSs around the world before CRV gave the all-clear. During this time, the fake front-end could have still posed a potential, but slim, risk if the attacker had kept their front-end host alive.
Fortunately, because the response was so fast, the attacker had a very limited window of opportunity before CRV users were put on high alert. Unfortunately, the address identified on Etherscan as the "Curve DNS Hijacker" still managed to send 335.0862 ETH, split 10 times into various amounts, to different addresses, and another 27.7 ETH through the privacy protocol TornadoCash (TC). Yes, even after the US placed the privacy tool on its sanctions list just the day before hackers were not stopped from using TC.
Thirty minutes of spreading the word as fast as possible was all it took to stop the bleeding, marked by the time-stamp of the last transaction with the malicious contract, but 1 hour and 25 minutes had already passed by the time the first alarm bell was rung and the damage had already been done. From the first transaction with the malicious contract at 7:07 PM to the last one at 8:55 PM UTC, it seemed the attacker had managed to get away with a total of approximately 362.7862 ETH. In other words, in just under 2 hours, given a ETH market price of around $1,700 at the time, approximately $616,700 of user funds were lost.
Users who thought they were using CRV, but were sending ETH to an attacker instead.
Curve Did Nothing Wrong
This hack had nothing to do with the CRV protocol itself, or their official front-end site. What happened here was called a DNS spoofing attack. CRV's domain name, curve.fi, was made to no longer point to the correct IP address. Users could have still used the real CRV front-end, as it was still being hosted, if they knew to manually navigate to 76.76.21.21 in a browser, but this is not widely known by most users and not at all user friendly.
This seems to be a common weakness of DeFi, or any other crypto-app for that matter, a vulnerability that has been grandfathered in from Web 2.0 conventions.
In this case it wasn't someone with admin privileges to CRV's domain that was compromised through a social engineering attack, like what happened to Axie Infinity's Ronin bridge. It also didn’t have to do with poor password management that gave the attacker access to CRV's account with the registrar. CRV really didn’t do anything wrong. It was specifically the NS of their domain registrar that was compromised, and it wasn't until 12:46 PM the next day that @iwantmyname shared their public statement to Twitter, where they reported that the "change occurred on 9th August around 7 PM UTC'' and was the result of “Cache poisoning”.
As mentioned above, CRV has since reassigned their domain to an authoritative NS, controlled by DigitalOcean, which should be much more secure as one of the most popular virtual private server (VPS) providers in the industry. At the time of writing, the exact method used to compromise iwantmyname's NSs is still being investigated.
A Breadcrumb Trail
Something that is kind of baffling is why the attacker only sent a small portion of the stolen funds: 27.7 ETH, or just over 7.6% of the total 362.7862 ETH sent from the address, which was receiving the stolen funds, to various exit addresses that was receiving the stolen funds. They showed us that they were fully aware of the ability of TC to hide stolen funds—after all that was the whole point in sanctioning TC the day before – why not send at least a full validator's worth of 32 ETH, or even all of it, through TC?
Of the 10 exit addresses the attacker used to unload from the primary address, which created the malicious contract and received the exploited funds, 7 were simply used to relay the total 292 ETH sent to them from the original attacking address to an exchange called FixedFloat. Another simply relayed their 20 ETH to Binance for some reason.
At 5:07 AM UTC on August 12, @cz_binance reported that "Binance froze/recovered $450k of the Curve stolen funds." This would account for the 292 ETH that was relayed to FixedFloat plus the 20 ETH that was relayed to Binance itself. They better have caught that one. This 312 ETH is almost exactly 86% of the total 362.7862 ETH stolen, so some funds must have been spent on gas, other fees, or maybe moved elsewhere by the attacker before the exchanges could freeze the funds.
When visiting FixedFloat’s website, one of the first things advertised is that they will allow swapping to Monero (XMR) and Z-Cash (ZEC), both privacy-preserving layer 1 blockchains. So perhaps it wasn't a mistake that the attacker sent funds to a centralized exchange, after all this hack was hopefully not easy to pull off, but why risk sending the money through a regulated centralized exchange as it resulted in all of those funds being frozen? Best guess is that maybe they were hoping to make use of other privacy preserving chains other than TC.
The remaining two exit paths looked like this. 23 ETH was sent to a relay address that bounced it to another which has a history of more than 185,000 transactions. This address has registered several ENS names in its history but otherwise appears to have been relatively careful not to compromise its owner’s identity. The last transaction leaving the malicious contract bounced the remaining 0.0862 ETH from the malicious contract to the Hashflow Bridge. Besides the input and output transactions required to bounce those funds this relay address has only one other interaction with an address registered under the ENS name anarchitect.eth. Anarchitect was first funded by another address that has received a transaction from FTX, but also appears to have interacted with one of the Nomad Bridge Exploiter. This address that may have created anarchitect.eth was also first funded by an address that has a history of receiving funds from FTX.
Lessons Learned
Ultimately, the big takeaways from this hack, minor as it was in comparison to some others, coming in at less than a million of hacked funds, are that Curve developers/admins did nothing wrong on their end, and their DeFi protocol didn’t fail. Everything that went wrong, that we know of, was Web 2.0 related. Something else to take note of is that the US sanctions on TC did absolutely nothing to prevent the hackers from washing at least some of their funds through it.
Something DeFi protocols, or any Web3 decentralized app (DApp) for that matter, can do to prevent similar attacks includes moving your front end exclusively to being hosted on IPFS and use ENS to direct your users to the appropriate host of the front end. By using a method like this a similar spoof cannot happen because you would need the private keys of the ETH address holding ownership of the ENS domain, or better yet a Gnosis Safe multi-sig would make that even more resilient. Requiring an attacker to compromise several individual private keys to be able to do what was done to CRV.
As we saw with this hack hundreds of thousands can be stolen in less than an hour. Luckily Binance has stated that they had recovered the vast majority of the funds, but that’s a little too close for comfort to rely on the attacker to make a mistake once they’ve already lifted the money. Relying on Web 2.0 technology is costing Web3 users dearly.
🛠 BANK Utility (BanklessDAO token)
With over 5,000 holders, BANK is one of the most widely held social tokens in crypto. So it bears asking, where are the best places to put our BANK to use? The five protocols below will allow you to deposit BANK in a liquidity pool and earn rewards. To get going, just click on the name, connect to the app, filter by BANK, and start earning passive income.


⚖️ Balancer
Balancer has two 80/20 liquidity pools, meaning that you are required to deposit 80% BANK and 20% ETH in the pool. There is one pool on Ethereum and another on Polygon. Once you’ve provided liquidity, you’ll receive LP tokens. Keep an eye out for opportunities to stake these LP tokens. There is nearly 500,000 USD in the two Balancer liquidity pools.
🍣 SushiSwap
SushiSwap has a 50/50 BANK/ETH pool. As with Balancer, you will receive LP tokens, and while you can’t stake them on SushiSwap’s Onsen Farm yet, you may be able to in the future. Liquidity providers earn a .25% fee on all trades proportional to their pool share. The SushiSwap pool has a little over 100,000 USD in liquidity.
⏛ Rari Fuse Pool
The Rari Fuse Pool allows you to borrow against your BANK or earn huge APY by providing assets like DAI to the pool. At present, all borrowing is paused for this pool. There is over 450,000 USD deposited in the Pool
🦄 Uniswap
The Uniswap V3 liquidity pool is 50/50 BANK/ETH, and provides a price oracle for the Rari Fuse Pool. By depositing in the Uniswap pool, you can earn fees and help enable borrowing on Rari. This pool currently has over 500,000 USD in liquidity.
🪐 Arrakis
You can also provide liquidity to the Arrakis Uniswap V3 pool. The ratio is about 2/1 BANK/ETH. This pool is new, and only has a bit more than $6,000 in liquidity. In the future, you may be able to stake your BANK/ETH LP tokens within the protocol to earn additional rewards.
AMM Tactics
Beginner Tactics
Best yields in the crypto bear market - Convex
Author: Ben Giove
How to use SushiSwap
Author: William Peaster
How to get the best prices using 1inch
Author: Jessica Salomon of 1inch Exchange
How to use Balancer V2
Author: William Peaster
Intermediate/Advanced Tactics
How to take a DeFi governance bribe
Author: William Peaster
KeeperDAO: ROOK takes Knight
Author: Lucas Campbell
🏆 BanklessDAO Cryptocurrency Challenge: Winner Announcement!
We’re not sure if the recent market upswing represents an escape from the bear’s clutch, but the world of BANK has been on the move with all portfolios increasing in value over the last half of the contest.
Before announcing the champion, here’s a description of the winning strategy: leveraging BANK and enjoying an outsized return as BANK value leapt over 50%. The next best strategy was to hold BANK, followed by purchasing GMI.
One person went all in. Congratulations for your 100% bet on the BANK accelerated portfolio Jengajojo! The 5000 BANK purse is yours!
Rounding out the top three spots, we have Jarlaxle in second, and a tie for third featuring EthHunter and affifes.
Thank you to all participants in the inaugural Challenge.
Get Plugged In
Event Highlights
DeFi Security Summit —Stanford, California— is the inaugural DeFi security event to address pressing DeFi vulnerabilities and mitigation strategies. The summit includes discussions and talks about DeFi vulnerabilities, cross-chain security, and audits. Confirmed speakers include Aave Head of Smart Contracts, Emilion Frangella, Nexus Mutual Founder Hugh Karp, and Optimism Security Engineer John Mardlin. August 27-28, 2022, Paul & Mildred Berg Hall, Stanford University, Stanford, California, USA.
DevCon Bogota—Bogota, Columbia—hosted by the Ethereum Foundation that’s geared toward developers, researchers, and movers within the Ethereum ecosystem. Devcon aims to deliver a holistic learning experience through panels and workshops. This conference is for builders of all kinds: developers, designers, researchers, client implementers, test engineers, infrastructure operators, community organizers, social economists, artists, and more. Oct 11-14 📌 Agora Bogotá Convention Center
ETH San Francisco—San Francisco California—Hailed as the West Coast’s premier Ethereum event of 2022, ETH San Francisco unites blockchain and crypto enthusiasts, as well as developers, industry experts, and tech companies. Discover more Ethereum events around the world here and check out the ETHGlobal site to get more updates about this and other upcoming events. November 3-5, 2022, San Francisco, USA.
🧳 Job Opportunities
Get a job in crypto! Do you like solving hard problems, care about building more efficient markets for everybody, and want to work at the frontier of decentralized finance? Rook is looking for full time contributors, with salaries ranging from $169,000-$722,000. There are positions ranging from engineering, recruiting, product marketing, copywriting, and design. Sound interesting? Sign up for our referral program and go full-time DAO.
2D Graphic Designer
Quantitative Analyst
🙏Thanks to our Sponsor
Oasis.app
Oasis.app was born as the frontend to access Maker Protocol and create DAI. It allows you to borrow DAI, exchange your tokens internally and multiply the exposure to your collateral (among the 30 available cryptoassets). Oasis.app is now the most trusted entry point to the Maker Protocol. The long term mission is to allow users to simply and easily deploy their capital into DeFi and manage it in one trusted place.
👉 Get started with the Oasis.app
👉 Follow them on Twitter
👉 Join their Discord